We are increasingly storing information on computers, online and other devices. Download.com.vn has shared with you the ways to secure iPhone, but you also need to secure your computer, especially laptops. People can access your Mac, access private files and sensitive information if you're not careful.
In this article, let's learn about 20 ways to secure your Mac to prevent your data from falling into the wrong hands. You don't have to apply them all, just pick a few methods that you feel are best for you.
See also: Summary of iPhone security ways that you need to know
1. Disable automatic login
The automatic Mac login feature is convenient, allowing you to log in to your account automatically. However, it is not safe. You may not be able to set a password for your account, which is never recommended.
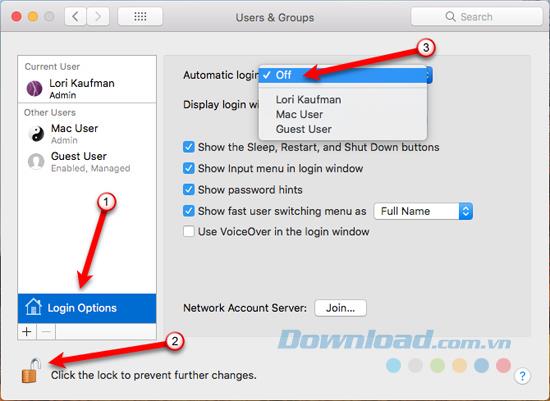
You should really disable this feature. To do that, go to Apple> System Preferences> Users & Groups . Then, click Login Options at the bottom of the user list on the left.
Next, click on the lock icon at the bottom of the dialog box and enter the password when prompted. This allows you to make changes in settings. Select Off from the Automatic Login list . You'll have to enter your password each time you boot your Mac, which is a bit inconvenient but useful to prevent someone who has an account and access to your data.
2. Protect user accounts with secure passwords
Besides disabling automatic login, you need to make sure you have a secure password for your user account. When setting up your Mac, you are asked to enter a password for the user account.
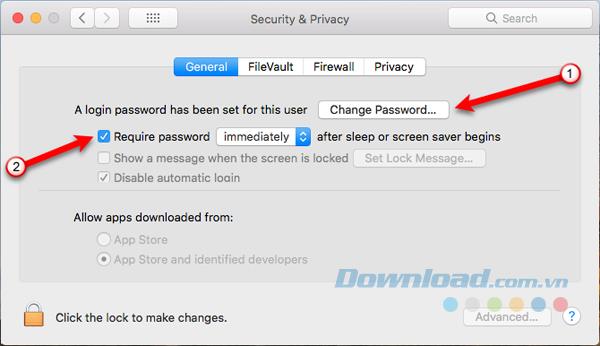
To keep your account safe, it's best to periodically change your password. Go to Apple> System Preferences> Security & Privacy . Select the General tab and click on Change Password .
In the popup dialog, enter the old password, then the new password you want to use and click Verify to verify the new password. Enter a password hint ( Password hint ) to help you remember the new password. Finally, just click Change Password .
You should also set your Mac password protection when it goes to sleep or when the standby screen starts. To enable this setting, check the Require password box . Choose the time your Mac goes to sleep, or the standby screen starts to ask for a password to return to your account. You should choose Immediately , especially if you are in public or anywhere else around you.
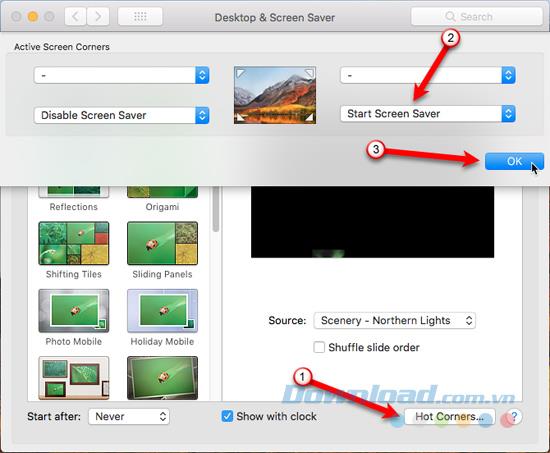
If you need to quickly get out of your Mac, you can easily turn on the standby screen right away with Hot Corners . To assign a hot corner to start the standby screen, go to Apple> System Preferences> Desktop & Screen Saver . Then click Hot Corners in the lower right corner of the dialog.
In the Active Screen Corners dialog box , select Start Screen Saver from the drop-down list for the angle you want to use and click OK . To activate the standby screen immediately, drag the mouse to the corner you selected.
3. Use a password manager
With online services growing as they are today, each person usually owns more than one account and a corresponding password for each of those accounts. Creating strong passwords helps you protect your account better, but it's also hard to remember every password for every account you use. When creating a strong password, you should follow three criteria:
- Every account needs a unique password.
- Use strong passwords with a combination of uppercase letters, lowercase letters, numbers and special characters.
- Change the password periodically.
To easily remember every password, you can take advantage of a password manager. Many password managers have the ability to generate strong passwords for you and store them.

See more: TOP 5 best password management software today
4. Activate Find My Mac
Find My Mac allows you to protect and recover a lost or stolen Mac. You can locate your Mac, lock it, or erase all data with Apple ID and another computer or your iPhone.
Before activating Find My Mac, you need to turn on Location Services by going to Apple> System Preferences> Security & Privacy . Click on the Privacy tab and select Location Services .
Next, click on the lock icon at the bottom of the dialog box and enter the password when prompted to make changes. Then, check the box Enable Location Services . Click the lock icon again to prevent any other changes.
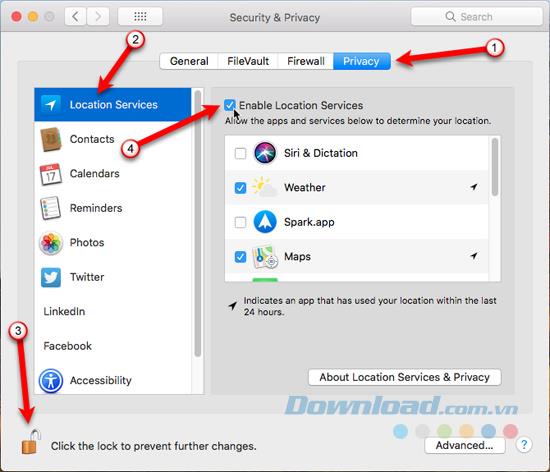
Once location services are turned on, click the left arrow at the top of the System Preferences dialog box to return to the main screen and click iCloud .
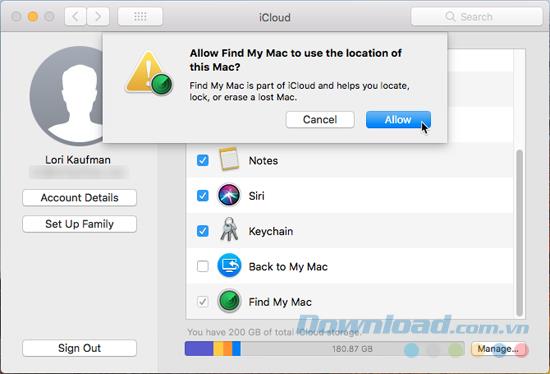
On the iCloud screen, check Find My Mac at the bottom of the list if it's not already selected and click Allow when prompted.
See also: Instructions for creating free iCloud and Apple ID accounts
5. Turn on guest accounts
Guest accounts work in tandem with the Find My Mac feature. If someone finds your Mac, you can locate it if that person logs on as a guest (because it's the only account they can access) and access the Internet using Safari .
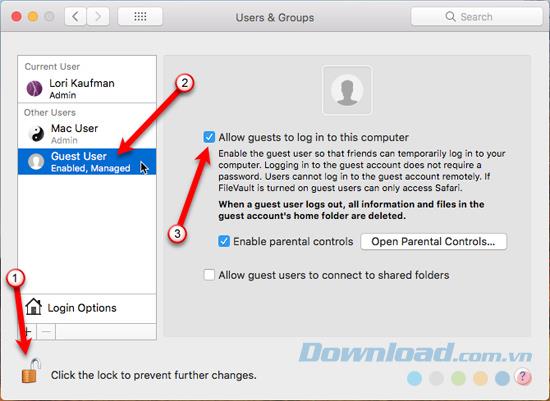
So to make sure guest accounts are enabled, go to Apple> System Preferces> User & Groups . Click on the lock icon at the bottom to make changes. Click on Guest User in the list and then tick Allow guests to log in to this computer . Click the lock icon again to prevent further changes.
6. Turn on the Firewall
Mac firewalls block traffic to specific applications. Therefore, firewalls are only useful if you have applications on your computer that you want to restrict information to. Firewalls on Mac are off by default.
So you don't necessarily need a firewall to secure your Mac. However, if you wish you can turn on the firewall by going to Apple> System Preferences> Security & Privacy . Click on the Firewall tab and lock icon at the bottom, enter the password to make changes. Then, click on Turn On Firewall .
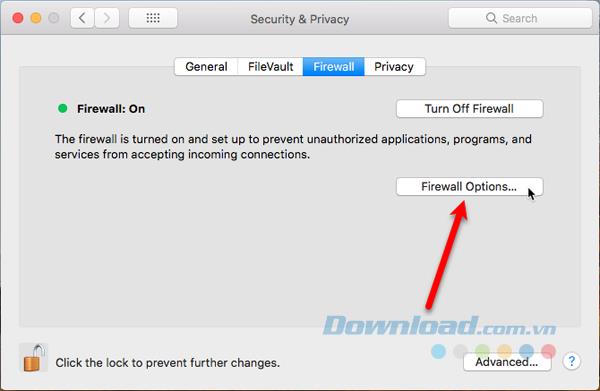
To configure firewall options, click Firewall Options . You will see a list of applications and services that can receive incoming connections. You can add to the list by using the plus icon below the list. You may have to do this if you run an application and it gives you an error message saying that it has been prevented from accepting an inbound connection.
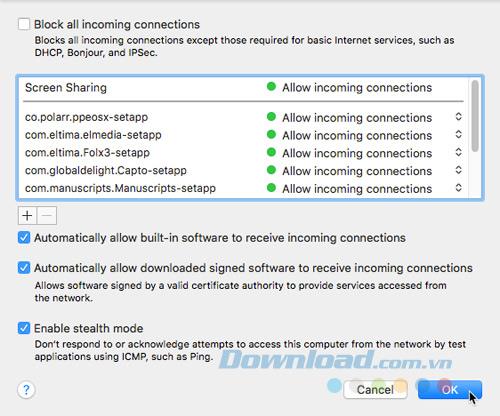
7. Turn on encrypting the whole drive using FileVault
FileVault is a utility available on Mac to encrypt all data on hard drive. When FileVault is turned on, the contents of the drive cannot be accessed without a password or recovery key.
FileVault is off by default. The inconvenience of having to type a password to open the file and the time it takes to encrypt your entire drive can be greater than the security that FileVault offers. Therefore, if you often use a Mac at home, FileVault is not an ideal solution. However, if you want, you can enable it in Apple> System Preferences> Security & Privacy and click on the FileVault tab .
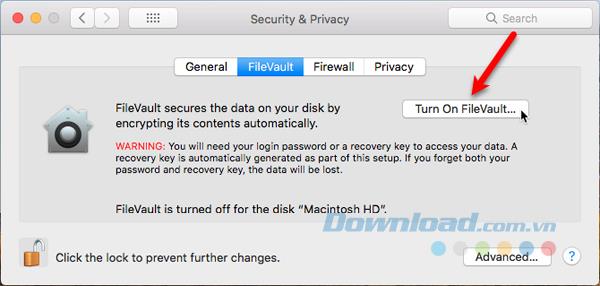
Click the lock icon at the bottom, enter your password to make changes. Then choose Turn On FileVault and follow the instructions to set it up.
8. Create an encrypted repository
On a Mac, DMG files are usually associated with installation applications. However, you can also use the DML file as an encrypted repository to store sensitive files and folders. This feature is like using a program like VeraCrypt on Windows.
You can create DMG files using the Disk Utility application, which is located in the Applications / Utilities folder . After opening Disk Utility, go to File> New Image> Blank Image and enter information for the DMG file, including the file name in Save As , Where to save the file and Size .
Be sure to select Encrytion type and enter the password when prompted to secure the DMG file.
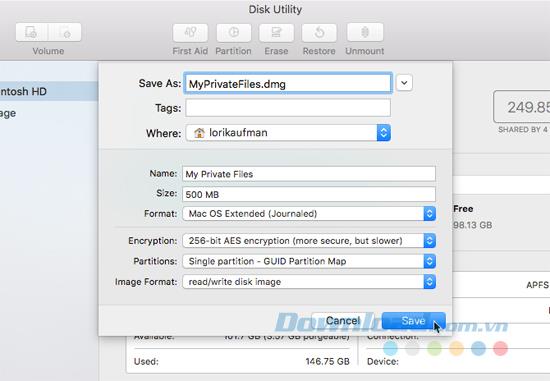
After the DMG file has been created, it will automatically open, displayed in the Finder and on the screen as a different drive. Now, you can move individual files and folders into DMG files. To lock it, push it away from the desktop icon like any external hard drive connected to your Mac. To reopen the DMG file, double click on the file and enter the password.
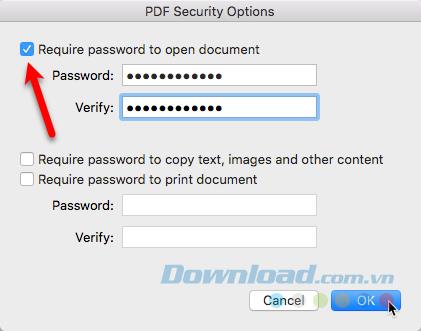
9. Protect files and folders with a password
There are many other ways to protect data on Mac. You can protect files and folders with a password in various ways.
10. Backup data
You can protect data with a password. If your Mac is lost or stolen, you can lock it or erase all data. So, what do you need to lose all your data, when you don't have any backups?
Macs include a very useful backup solution called Time Machine . If you use an external hard drive with a large storage capacity, you can partition it first, using one for Time Machine backups and another for storing files.
Once you've partitioned an external drive, go to Apple> System Preferences> Time Machine .
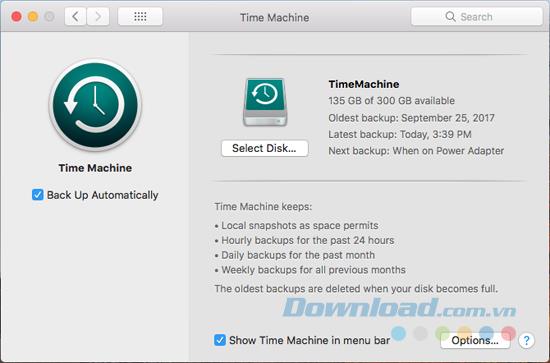
After the initial backup, you can automatically start the backup using Time Machine (check the Backup Up Automatically ). If you want to start a manual backup before the automatic backup takes place, check Show Time Machine in the toolbar menu. Then, access the Time Machine menu and start backing up from there.
11. Check your privacy and security settings
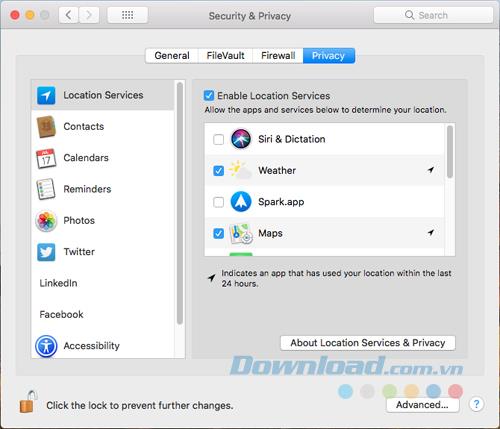
The Privacy tab in Security & Privacy allows you to control which apps have access to specific data on the Mac. You can disable Locations Services completely on the Privacy tab , but keep in mind that Find My Mac will not work if you do so. Ideally, you should disable each application individually in the list on the right.
Apps listed on the left, such as Contacts, Calendar, and Reminders, allow other applications to access the data stored in them. You can specify which applications have access to that data.
You can add social networking accounts like Facebook , Twitter and LinkedIn in the same place in System Preferences like adding email accounts. On the Privacy tab of Security & Privacy , you can choose which apps have access to information in your social networking accounts.
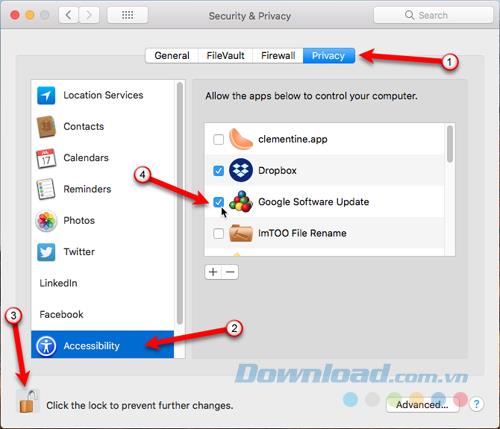
The Accessibility part of the Privacy tab is different from the Accessibility option on the main System Preferences screen . The Accessibility options on the Privacy tab allow you to control which applications can control the Mac in certain ways. You will notice that some applications may not work until you enable them on this screen.
12. Always update the software and system
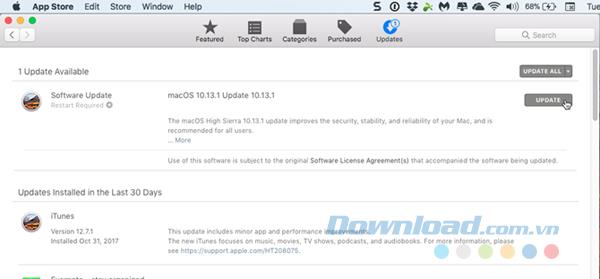
Outdated software can cause problems, especially if you ignore security updates. Apple usually releases updates for both macOS and firmware that control many aspects of the system to patch security holes that put Macs at risk of attack.
Most updates can be installed on the Mac App Store in the Updates tab . By default, the system notifies you when it or any updates are available. You should install updates because they are released to keep applications and systems up to date.
13. Restrict which applications can run on Mac
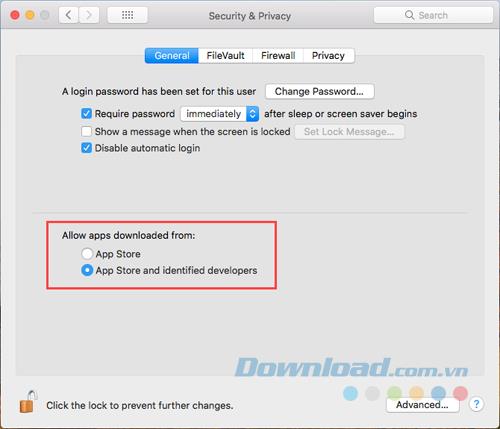
Macs have a feature called Gatekeeper that allows you to choose where applications can be installed. You can choose to allow applications only from the App Store or from the App Store and from identified manufacturers. To select one of these options, go to Apple> System Preferences> Security & Privacy> General.
There was once an option for installing applications from anywhere, but it was removed on macOS Sierra. This is probably a response to the Gatekeeper vulnerability discovered in 2015. Some applications can bypass the Gatekeeper security features completely.
You can still install applications from anywhere, but you must allow individual applications on the General tab in Security & Privacy in System Preferences.
Apple also introduced System Intergration Protection (SIP) on OS X 10.11 El Capitan. SIP is designed to protect the most vulnerable parts of Mac operating systems. It prevents a user with root access (using the sudo command in Terminal ) from modifying specific areas on the hard drive where the operating system is installed.
14. Test the Persistent application
Long-term applications on Macs like startup programs on Windows. They start simultaneously with the Mac and maintain while you use the computer. Some examples that check for application updates are Google Chrome and Microsoft Office.
While long-term applications can be useful, malware also uses long-term applications to sneak into your system and operate without your attention. Malware can be hidden in many places in the file system so it can start when you start your Mac.
The task of tracking all potential locations where mailware can hide is a heavy task, but there are two free applications that can help you. KnockKnock scans these locations and tells you what is there. It is not a malware scanning application, so it will not tell you whether it is dangerous or not. But, Google search can help research anything you can't recognize.
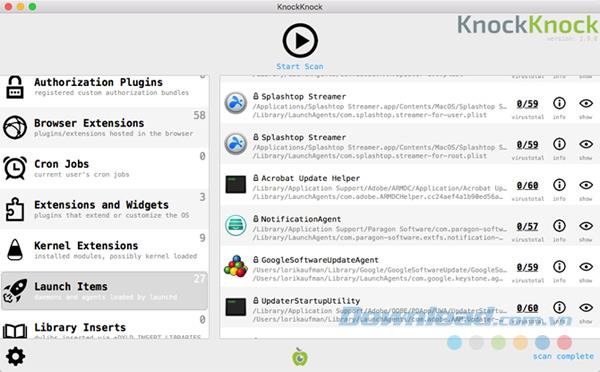
The second application is BlockBlock from the same place as KnockKnock, exists on the menu bar and runs in the background. It observes all permanent application installation locations. If an application tries to install continuously, a dialog box displays telling you and provides an option for you to allow or ban it.
BlockBlock is not an anti-malware application, so it does not know which long-term application is legal and what is malware. So you have to do your own research on Google.
15. Scan for malware
There are many types of malware, besides disguising themselves as long-term applications. Although Macs don't have as much malware as Windows does, more and more malware is targeting Macs. Therefore, do not be subjective.
The Mac already has a malware removal tool called Xprotect, which often runs in the background. Therefore, you do not need to install additional anti-malware on your Mac. If you feel you need to add an extra layer of protection, you can install the Bitdefender Virus Scanner application.
Download Bitdefender Virus Scanner for Mac
Bitdefender Virus Scanner is free and easy to use. It can detect and remove all types of malware, including viruses, spyware, trojans, keyloggers, worms and adware. Bitdefender Virus Scanner does not install any system monitoring software but slows down the system process. But this also means that you need to run it manually to scan the system for malware.
Malwarebytes Antimalware is a well-known application that focuses on finding and removing adware that hides code in certain applications that force ads to be displayed on computer screens or on web pages on browsers.
16. Use the VPN service
If you use your Mac in a public place like a coffee shop or office, you should use a virtual private network (VPN) service to add an extra layer of protection. A VPN encrypts data before it is sent over the Internet. It keeps you safe by hiding your online presence.
You will not notice any difference when browsing and downloading files. But, anyone on the same shared Wi-Fi network will be prevented from stealing data to and from your computer. Some VPNs for Mac you can choose like TunnelBear, NordVPN ...
Download TunnelBear for Mac Download NordVPN for Mac
17. Adjust privacy settings on Safari
Besides installing Security & Privacy on the System Preferences of your computer system, Safari has many settings that make browsing the web more private. However, private browsing is not as secure as you think it is because you can still be tracked.
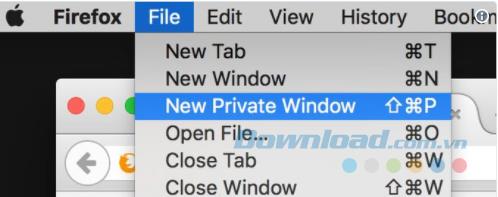
Private browsing is useful for hiding where you use the Internet on your own computer. Others who use your computer will not see the website you have visited or the searches you have made. To enter private browsing mode in Safari, you go to File> New Private Window or press Cmd + Shift + N .
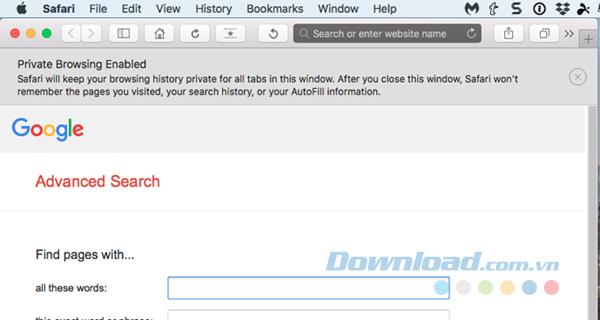
You can also clear browsing history, cookies, and cache data from websites you visit on regular Safari browser windows by going to Safari> Clear History or History> Clear History . You can also go to History> Show All History and click on Clear History at the top of the page. The Show All History page also allows you to delete the browser history individually.
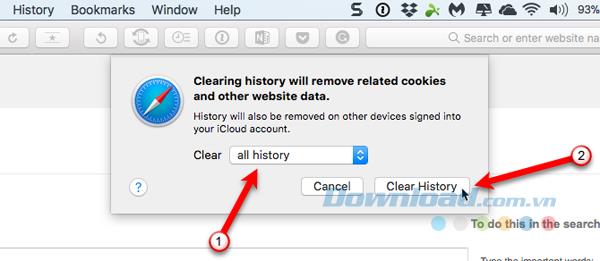
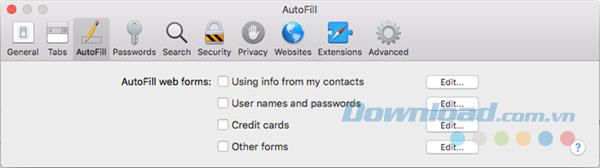
If you don't want Safari to store usernames and passwords or other personal data you enter on the web, go to Safari> Preferences and click on AutoFill in the toolbar at the top. Make sure all the AutoFill web forms boxes are unchecked.
18. Use HTTPS everywhere
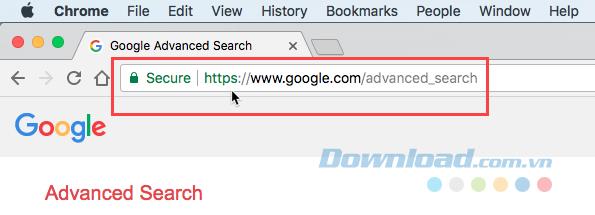
When you visit a website, usually the data is transmitted in pure form, which means that anyone can access the data while it is in the process of transmission. Websites like banks, webmail services and online shopping sites all provide secure connections. You can identify a secure connection by looking at its web address with HTTPS instead of HTTP.
19. Check what you are sharing
There are many things you can share from your Mac such as files, monitors, printer connections, Internet and Bluetooth. When a sharing service is turned on, it's like adding a new door or window to your home. You can lock the door or window (requires a password to access the sharing service), but that can't guarantee that no one has intruded.
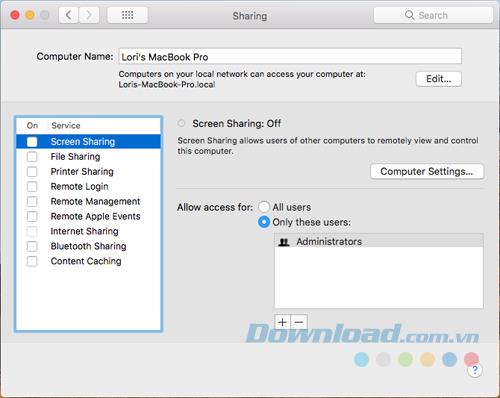
You should turn off sharing services when you are not using them. Go to Apple> System Preferences> Sharing . Make sure all the boxes in the On column in the list on the left are unchecked.
20. Activate two-factor authentication wherever possible
Two-factor authentication is a method of signing in to a website and a service that uses more than one password. 2FA requires what you know (turn on the password) and what you need (usually a mobile device). You enter the password, then a code is sent to the phone where you must enter it into the website to complete the login process.

Social friends like Facebook and Twitter offer 2FA and cloud backup services like iCloud , Dropbox , Google Drive and OneDrive .