How to Check Purchase History on Apple App Store
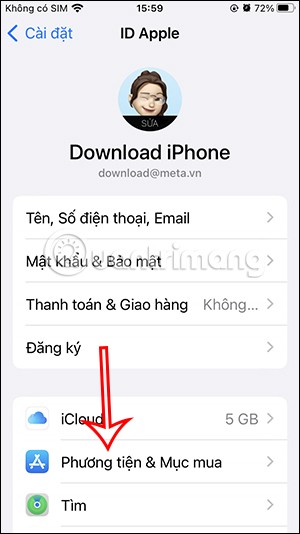
Through your purchase history on the App Store, you will know when you downloaded that app or game, and how much you paid for the paid app.
Firewall - A firewall is a network security system that monitors traffic going to and from devices connected to a network (usually the Internet) and acts as an intrusion detection mechanism to prevent attack. Such technology can exist in the form of a software package that can be installed on personal computer devices or hardware-based walls that often run in specialized systems to protect the entire network. before the hacker.
While the latter usually offers more benefits in intrusion prevention efforts, they are also more expensive and more complex than free firewall software available. In this article, Download.com.vn will introduce you to 6 best free firewall software that you can install on your Windows device.
ZoneAlarm is one of the oldest and most popular firewall programs for Windows and comes in two versions. The free version provides most of the basic features that you would expect to have on a modern firewall and the paid version offers many advanced features. The free version comes with the ability to hide open ports and identify as well as isolate suspicious traffic.
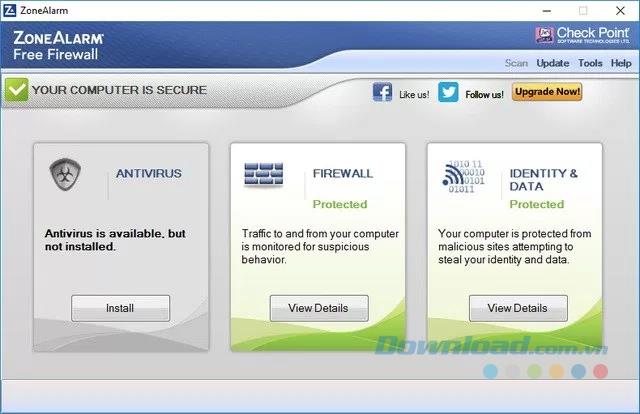
The latest version of the software also connects to DefenseNet to receive real-time security updates on new threats. Overall, ZoneAlarm is one of the most comprehensive and customizable third-party firewall programs you can install for your computer.
However, along with the advantages, ZoneAlarm also has its own problems. First, the company gradually trimmed the best features of the program on the free version that no longer came with the HIPS protection system. In addition, the program conflicts with some third-party antivirus programs, but works well with Windows Defender.
ZoneAlarm has really done what it can do so far. However, if you want a full-featured firewall with a free HIPS protection system, Comodo FireWall is the choice you should consider. The software comes with an active Defense + monitor. Comodo also gives users a great level of control over what programs can and cannot access the Internet and comes with a memory firewall feature that seeks protection against buffer overflow attacks. The program also provides sandbox protection, ad blockers as well as custom DNS servers.
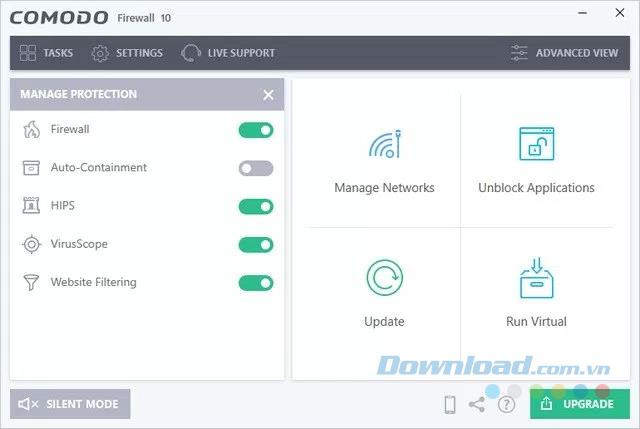
Comodo Firewall is probably the best feature-rich free firewall you can use on your computer, but make sure you choose manual settings instead of the default settings to prevent installation. Put all the extra software that comes with the program.
PeerBlock is a firewall program that works by blocking traffic to and from predefined IP addresses.
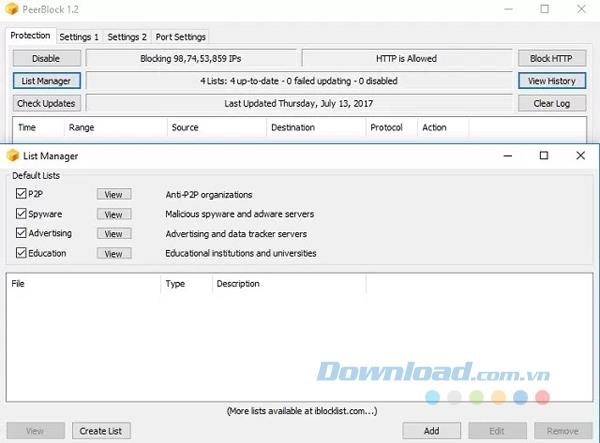
The program blocks both outgoing and incoming connections, but the user has the final say in the blocked and unblocked IP range. You can use many free public lists from I-Blocklist, or even create your own IP blacklist that can then be used to block traffic.
Once installed, you will be prompted to configure the software so that it can download multiple lists containing IP addresses of well-known adware vendors, spyware wholesalers, and government agencies. or organized against p2p. When you select your categories, the list will be downloaded and those IP addresses will be added to your blacklist and updated automatically at regular intervals without you having to do anything. .
Although the program itself is not maintained actively, the latest version is still stable, compatible with Windows 10 and can update the filter list periodically. However, given the sensitive nature surrounding peer-to-peer protocols, you should still sign up for a VPN service if you're a heavy torrent downloader.
Tinywall's USP is the program that uses the least system resources on the list, it only takes up about 1MB of your disk space after installation. However, it is not a stand-alone firewall program that is designed to work with the existing Windows Firewall, to control some of its features. Unlike some of the programs mentioned in the list, Tinywall does not use annoying popups that can often disturb your work.
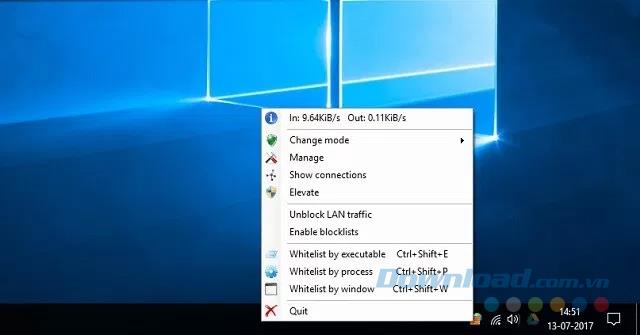
All settings and configuration of the program are accessible from a popup menu that may take some time to get used to.
While the other firewalls on the list are well-known and have been around for almost a decade, GlassWire has been in the market for only a few years. It is essentially a network monitoring tool in some respects, but also allows you to manually block any incoming or outgoing traffic that you feel suspicious.
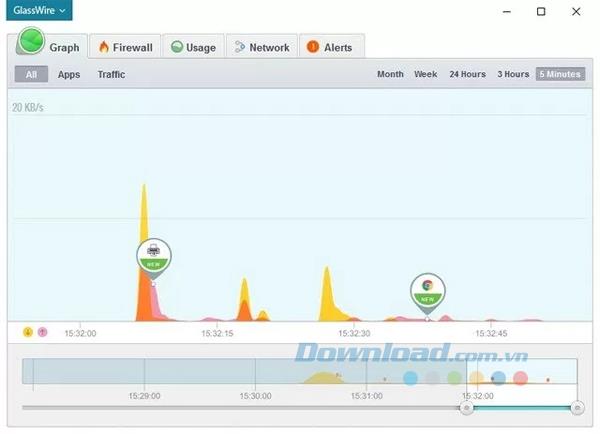
GlassWire records network activities on computers and creates easily distinguishable graphs that are classified by traffic type, application and geographic location. Although this is a very small tool to monitor your connection for more granular control, it is not a full-featured firewall program and actually relies on Windows Firewall to do all the blocking. .
Many people probably don't realize this, but Windows installations come with a built-in firewall from Microsoft. Since Windows XP, this firewall software has grown significantly and is now one of the most effective and least invasive firewall programs available on Windows-based systems. In terms of advantages, the software has passed all open and theft gateway tests and does not bother users with a series of popup alerts like other feature-rich firewall software.
On the downside, outbound protection is often suspected, but unless you have a computer filled with malware that makes all sorts of unauthorized connections steal your bandwidth and potentially push. putting your device at risk, Windows Firewall is all you need.
Firewalls are an important part of computer security and, if used correctly and in combination with anti-malware software, will protect you from a lot of dangerous situations.
Through your purchase history on the App Store, you will know when you downloaded that app or game, and how much you paid for the paid app.
iPhone mutes iPhone from unknown callers and on iOS 26, iPhone automatically receives incoming calls from an unknown number and asks for the reason for the call. If you want to receive unknown calls on iPhone, follow the instructions below.
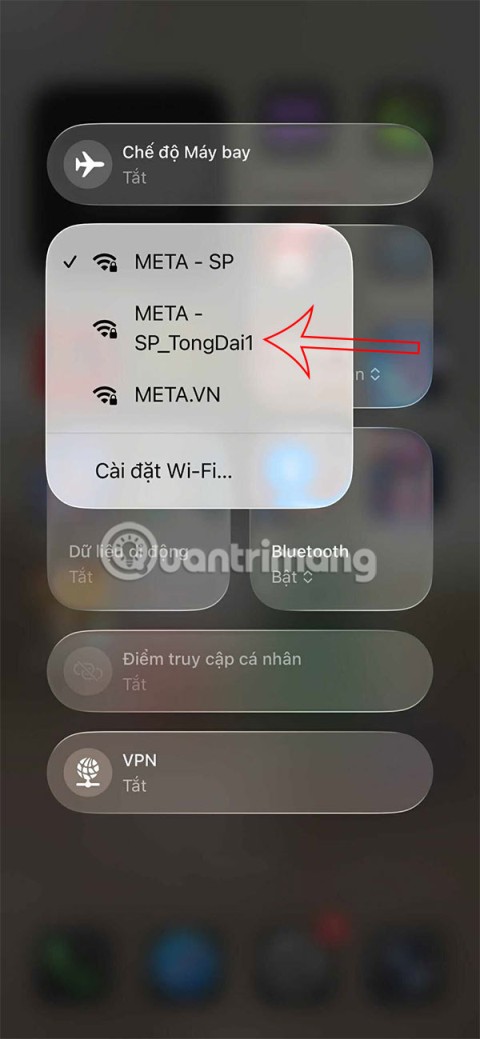
Apple makes it easy to find out if a WiFi network is safe before you connect. You don't need any software or other tools to help, just use the built-in settings on your iPhone.
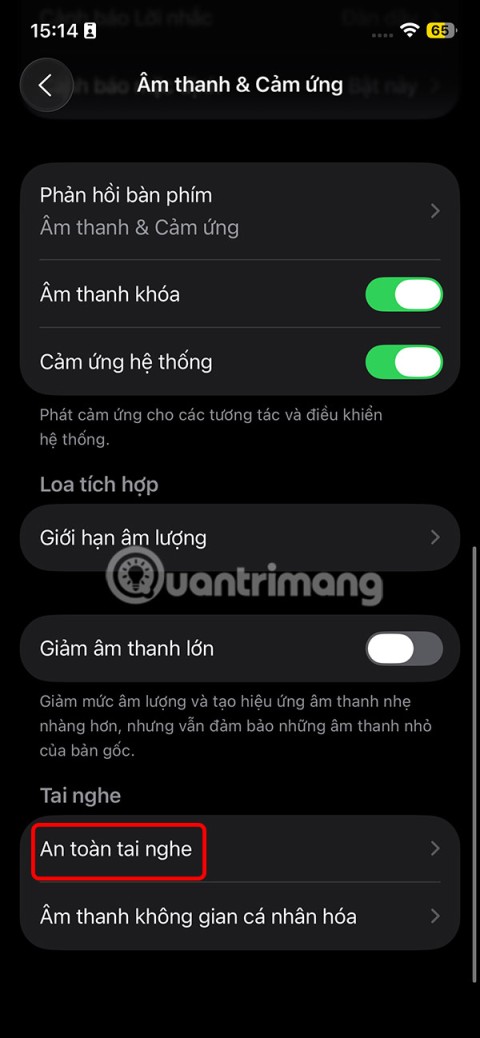
iPhone has a speaker volume limit setting to control the sound. However, in some situations you need to increase the volume on your iPhone to be able to hear the content.
ADB is a powerful set of tools that give you more control over your Android device. Although ADB is intended for Android developers, you don't need any programming knowledge to uninstall Android apps with it.
You might think you know how to get the most out of your phone time, but chances are you don't know how big a difference this common setting makes.
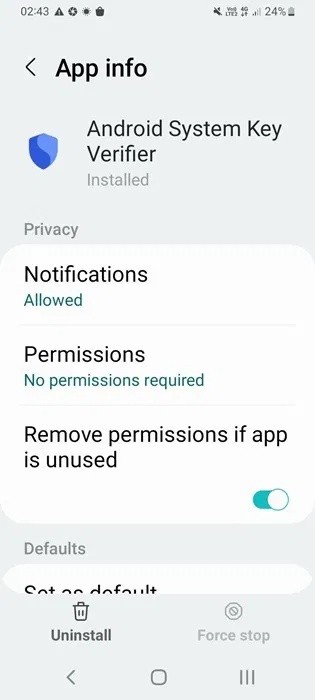
The Android System Key Verifier app comes pre-installed as a system app on Android devices running version 8.0 or later.
Despite Apple's tight ecosystem, some people have turned their Android phones into reliable remote controls for their Apple TV.
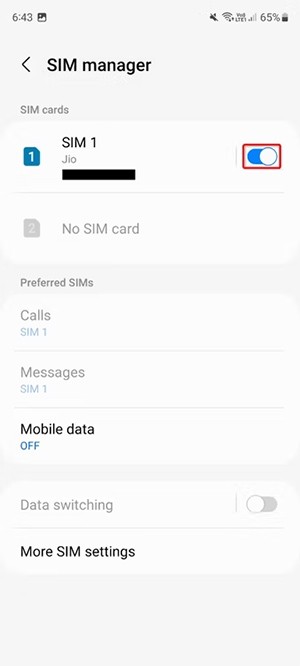
There are many reasons why your Android phone cannot connect to mobile data, such as incorrect configuration errors causing the problem. Here is a guide to fix mobile data connection errors on Android.
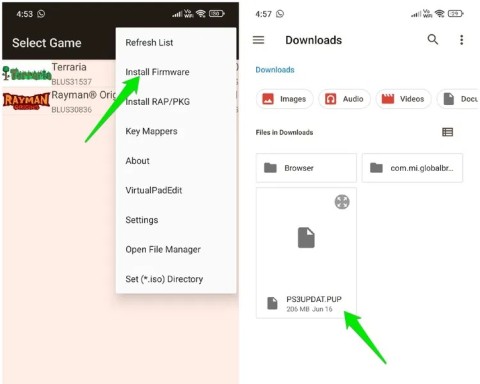
For years, Android gamers have dreamed of running PS3 titles on their phones – now it's a reality. aPS3e, the first PS3 emulator for Android, is now available on the Google Play Store.
The iPhone iMessage group chat feature helps us text and chat more easily with many people, instead of sending individual messages.
For ebook lovers, having a library of books at your fingertips is a great thing. And if you store your ebooks on your phone, you can enjoy them anytime, anywhere. Check out the best ebook reading apps for iPhone below.
You can use Picture in Picture (PiP) to watch YouTube videos off-screen on iOS 14, but YouTube has locked this feature on the app so you cannot use PiP directly, you have to add a few more small steps that we will guide in detail below.
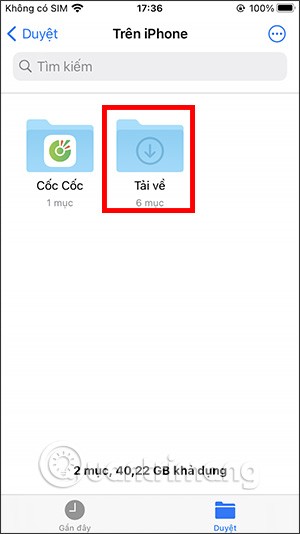
On iPhone/iPad, there is a Files application to manage all files on the device, including files that users download. The article below will guide readers on how to find downloaded files on iPhone/iPad.
If you really want to protect your phone, it's time you started locking your phone to prevent theft as well as protect it from hacks and scams.