Analyzing an Attack (Part 3)
In part 2 of this series, we have left all the necessary information required for an attack on the victim's network.
In part 2 of this series, we have left all the necessary information required for an attack on the victim's network.

Microsoft Office has supported ActiveX for years as an option for document extensibility and automation, but it's also a serious security vulnerability.

This series will be based on a network vulnerability. What will be introduced in the article is already a real attack, starting from reconnaissance to enumeration, exploiting network services and ending with exploitation strategies sending notifications. All these steps will be observed at the data packet level, and then explained in detail.
The world-famous cybersecurity company Fortinet has just officially confirmed that a large amount of user data was stolen from the company's Microsoft Sharepoint server, and was posted on a hacker forum early in the morning of September 15.
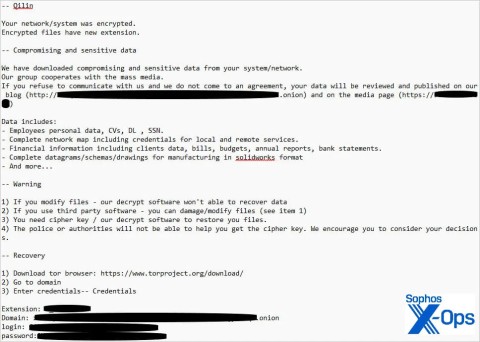
A new strain of ransomware called Qilin has been discovered using a relatively sophisticated, highly customizable tactic to steal account login information stored in the Google Chrome browser.
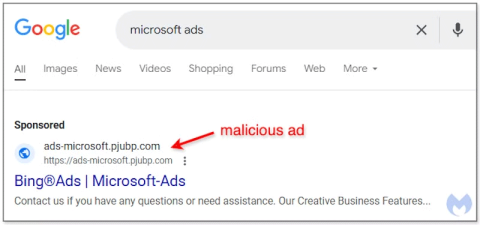
There is a dangerous trend being deployed by the global hacker community, which is abusing the Google Ads platform to spread malicious code.
We showed you in part one the information that can be observed while opening the packet sequence sent by Nmap. The sequence sent starts with an ICMP echo response to determine if the computer or network has been assigned an IP address.