Analyzing an Attack (Part 3)
In part 2 of this series, we have left all the necessary information required for an attack on the victim's network.
With Google's popularity, scammers are taking advantage of the company's services to commit malicious acts. Bad actors are pushing malicious ads onto Google's results pages, and while this tactic isn't new, this new method is aimed at stealing users' Microsoft login credentials.
Fake Microsoft Ads Stealing People's Accounts
In a report by Malwarebytes, the attack starts when someone searches for a Microsoft Ad program. Google serves up relevant sponsored links for the search term, and one of them is a fake copy of the Microsoft Ads site. It has a different URL than the real site, which is usually a giveaway.
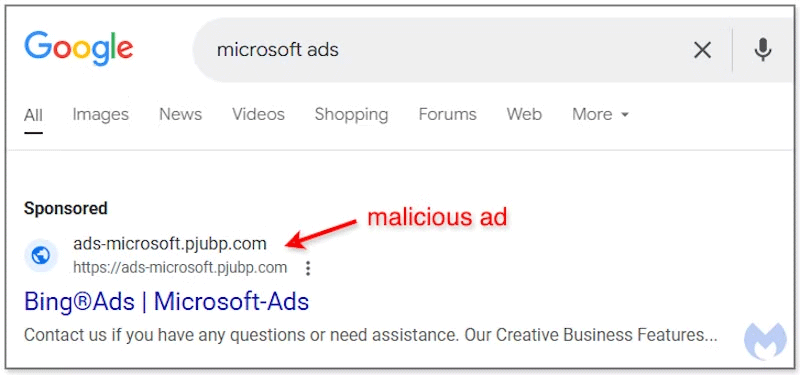
However, people often trust Google's search results so much that they blindly click on the first result they see. And if the scammer is skilled enough, they can make their sponsored links look almost identical to the real ones, even if the URL looks strange.
The fake Microsoft Ads site has a number of measures in place to keep unwanted visitors out. For example, if a bot tries to parse the site or someone visits via VPN, the site will serve a fake landing page to distract them. And if you try to go directly to the URL without going through the fake ad, the site will instead show you a video of Rick Astley singing “Never Gonna Give You Up.”
However, if you access it through Google Ads, you'll see a fake Microsoft login page asking you to enter your username, password, and two-factor authentication code. If you provide this information, the scammer can use it to steal your Microsoft account.
Given the way the attack targets people who want to use Microsoft Ads to advertise their products, it's unlikely you'll see it. However, it's a good example of how these scams work, as they can impersonate almost any website.
In part 2 of this series, we have left all the necessary information required for an attack on the victim's network.
Microsoft Office has supported ActiveX for years as an option for document extensibility and automation, but it's also a serious security vulnerability.
This series will be based on a network vulnerability. What will be introduced in the article is already a real attack, starting from reconnaissance to enumeration, exploiting network services and ending with exploitation strategies sending notifications. All these steps will be observed at the data packet level, and then explained in detail.
The world-famous cybersecurity company Fortinet has just officially confirmed that a large amount of user data was stolen from the company's Microsoft Sharepoint server, and was posted on a hacker forum early in the morning of September 15.
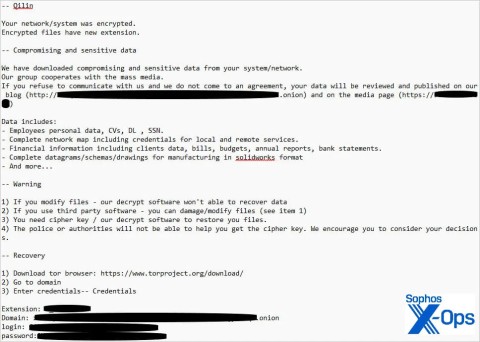
A new strain of ransomware called Qilin has been discovered using a relatively sophisticated, highly customizable tactic to steal account login information stored in the Google Chrome browser.
We showed you in part one the information that can be observed while opening the packet sequence sent by Nmap. The sequence sent starts with an ICMP echo response to determine if the computer or network has been assigned an IP address.
Tired of Microsoft Teams workflows and Power Automate errors halting your productivity? Get step-by-step solutions to common issues like authentication failures, timeouts, and flow errors. Fix them in minutes and automate effortlessly!
Facing Microsoft Teams "Download Error" on MacBook? Discover proven troubleshooting steps to resolve download failures quickly, from cache clears to reinstalls, and get back to smooth teamwork.
Tired of the frustrating Microsoft Teams "Where is Teams" Folder Error? Discover proven, step-by-step troubleshooting fixes to resolve it quickly and restore smooth teamwork. Latest methods included!
Frustrated by Microsoft Teams JavaScript Error on desktop app? Discover proven steps to fix it fast: clear cache, update, reset, and reinstall. Get back to seamless collaboration in minutes!
Struggling with Microsoft Teams "Guest Login" Error? Discover step-by-step fixes, from quick cache clears to admin settings, to resolve guest access issues fast and collaborate seamlessly. Updated with the latest tips!
Tired of the Microsoft Teams "For PC" download error blocking your work? Follow our proven, step-by-step guide to resolve it quickly and get Teams running smoothly on your PC today.
Struggling with Microsoft Teams "Windows 7" login error? Discover step-by-step fixes for this frustrating issue on Windows 10/11. Clear cache, edit registry, and more – get back to seamless collaboration today!
Tired of Microsoft Teams Error Code 0x80070005 blocking your meetings? Follow this 2026 guide with step-by-step fixes for access denied issues. Get Teams running smoothly in minutes!
Master the installation of the Microsoft Teams Add-in for Outlook 2026 effortlessly. Boost your productivity with seamless scheduling and meetings. Follow our proven, up-to-date steps for instant success!
Struggling with Microsoft Teams "License Error" 2026? Discover proven, step-by-step solutions to resolve it fast. Clear cache, check licenses, and get back to seamless collaboration—no IT help needed!
Whether youre in your 50s, 60s, or even 70s, its not too late to prioritize your health and put yourself first. Here are the best exercises for people 50 and older.
Struggling with Microsoft Teams Error Caa50024 on Windows 10/11? Follow our step-by-step fixes to resolve crashes and launch issues quickly. Latest proven solutions for seamless teamwork.
Stuck with Microsoft Teams login error AADSTS50011? Discover proven, step-by-step fixes to resolve the reply URL mismatch issue and log in seamlessly. No tech skills needed!
Tired of the frustrating Microsoft Teams "Win 7" Compatibility Error blocking your meetings? Get instant fixes with our step-by-step guide, including workarounds for older Windows versions. Resolve it now and stay connected!
Tired of the endless Microsoft Teams "Error R" restart loop? Get step-by-step fixes to solve Microsoft Teams Error R quickly. Clear cache, reset, reinstall & more for smooth collaboration. Works on Windows, Mac & web.