Microsoft reveals how Windows 10 and Windows 11 block keyloggers

In the early 2000s, Windows operating system security relied heavily on third-party antivirus software.
Keyloggers are extremely dangerous programs that hackers install on any user's system with the aim of stealing passwords, credit card information, etc. Keyloggers store all the keystrokes that users perform on the computer and provide hackers with important user information.
Each type of keylogger is dangerous because they can record your keystrokes, track your every activity and can record Open sites.
If you are using a computer with a Keylogger installed, it means that your important information can be easily stolen. Therefore, the best way is to check if your computer has a Keylogger installed or not. In the article below, WebTech360 will guide you on how to find and completely remove keyloggers on your system.
If you don't know much about keyloggers, don't miss this article: Learn about keyloggers
How to find and remove keylogger on computer
There are several signs that indicate a keylogger attack on your system. Here are the most common signs:
Use Task Manager to detect whether a Keylogger is installed on your system or not, it's very simple, just follow the steps below:
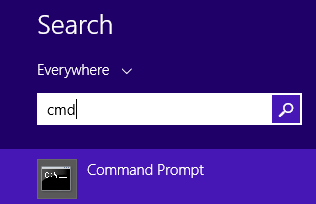
First open Command Prompt by typing cmd in the Search box on the Start Menu and then clicking Command Prompt on the search results list.
Next, on the Command Prompt window, type the command below and press Enter:
netstat –ano
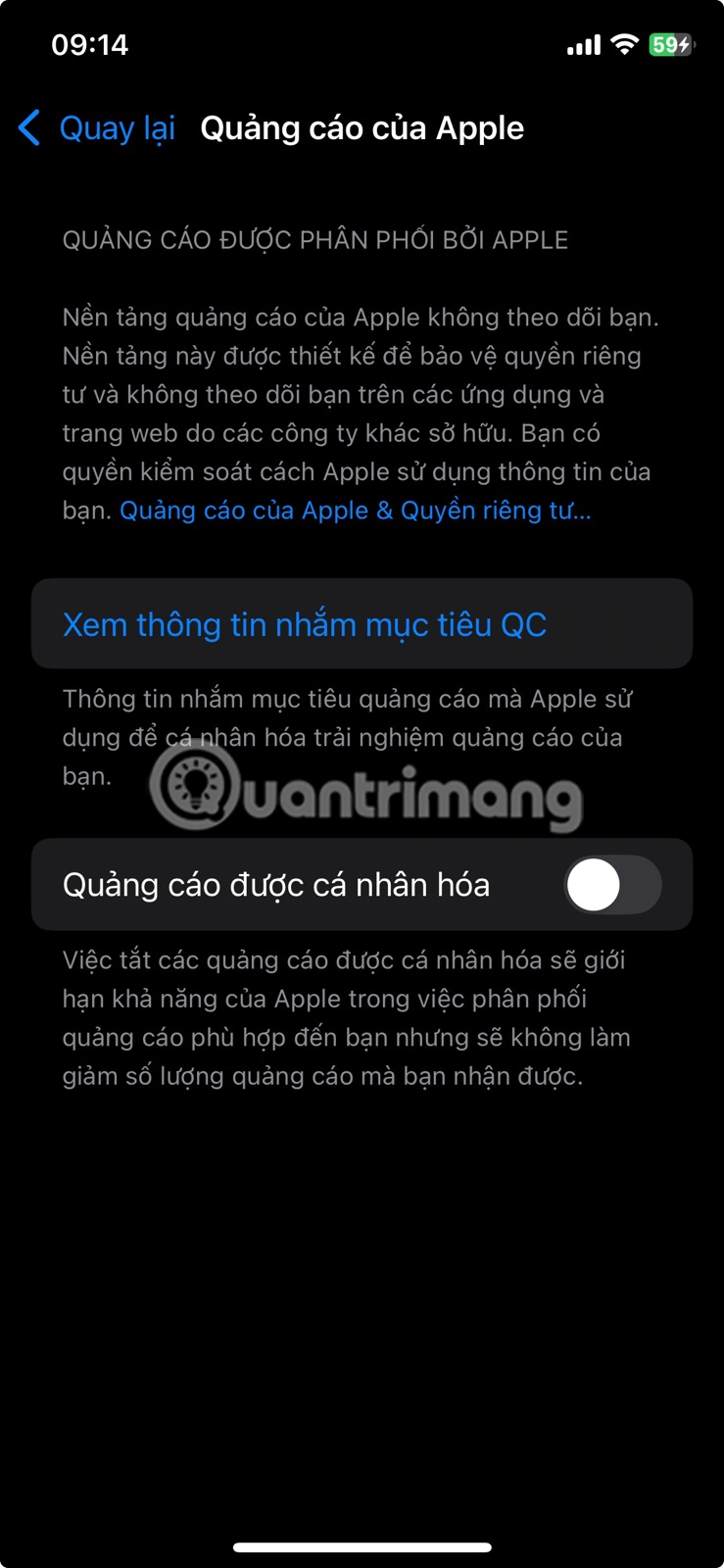
At this time, the Command Prompt window will display as shown below:
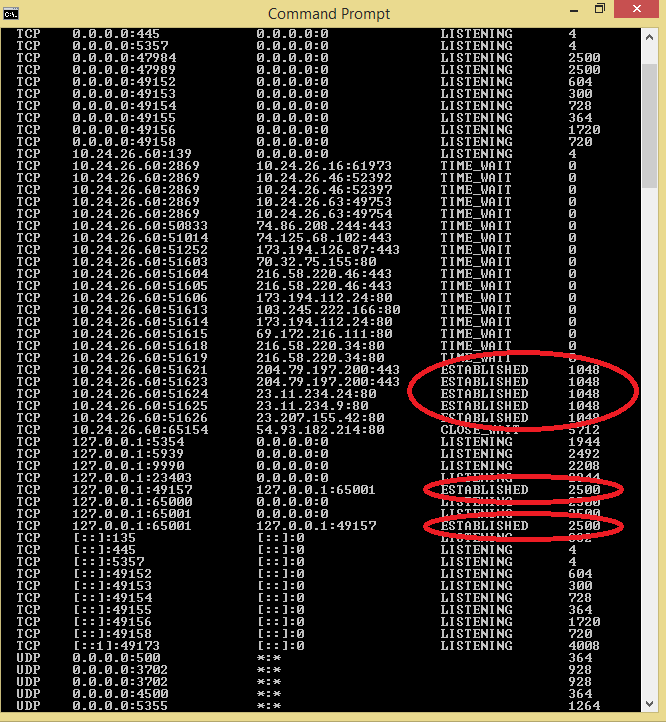
The data you receive will be displayed in 5 columns. You only need to pay attention to the rows that are set to Established .
In the illustration above you will see 2 PIDs set as Established, the first value is 1048 and the second value is 2500.
Next open Task Manager and go to the Details tab .
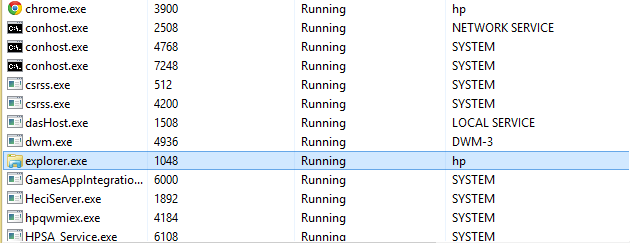
Now you can clearly see explorer.exe has an ID of value 1048. However, this is an important system service, so it can be confirmed that this is a safe program, not a keylogger.
Next go back to the Task Manager window again and find the process with PID 2500.
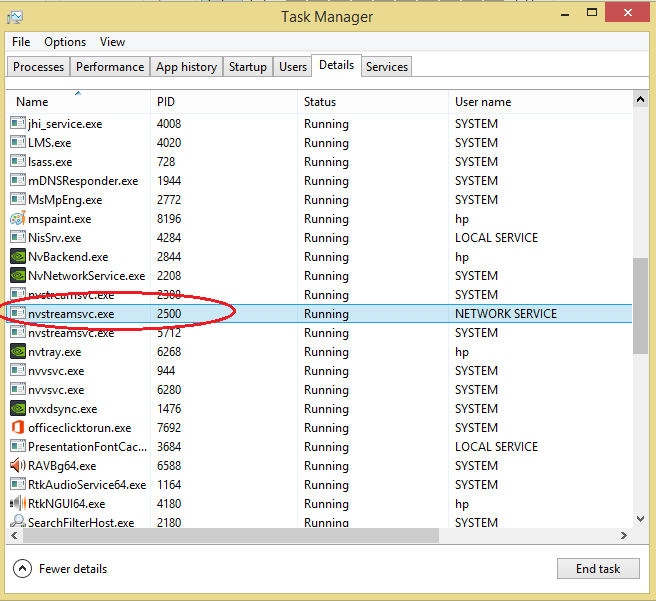
You will see nvstreamsvc.exe with ID 2500. However, after investigating, nvstreamsvc.exe is a program installed by nvidia with the graphics card. Therefore, it can be confirmed that the system does not have any keylogger installed.
Follow the same steps to check if your system has any keylogger installed?
Sometimes in some cases keyloggers can be found in the programs you install on your system, if the hackers do not hide these programs.
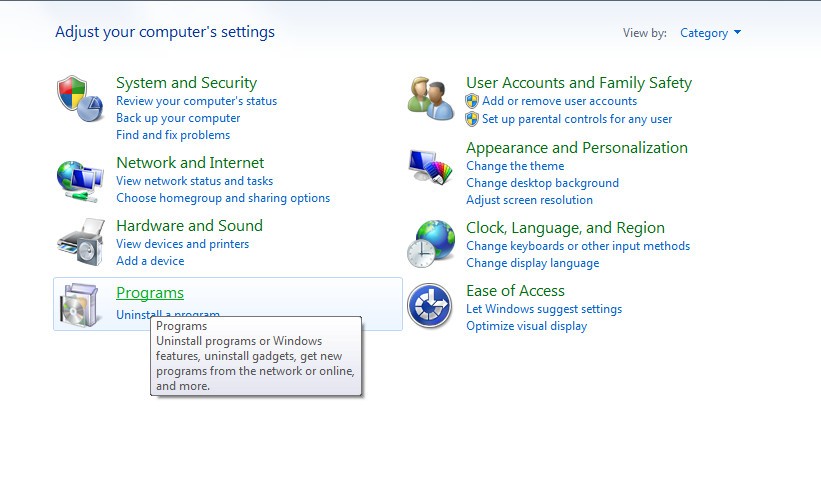
Now the screen displays a list of all the programs you have installed. If you find any programs that you did not install, it is likely that those programs were installed by hackers. Right-click on that program and select Uninstall .
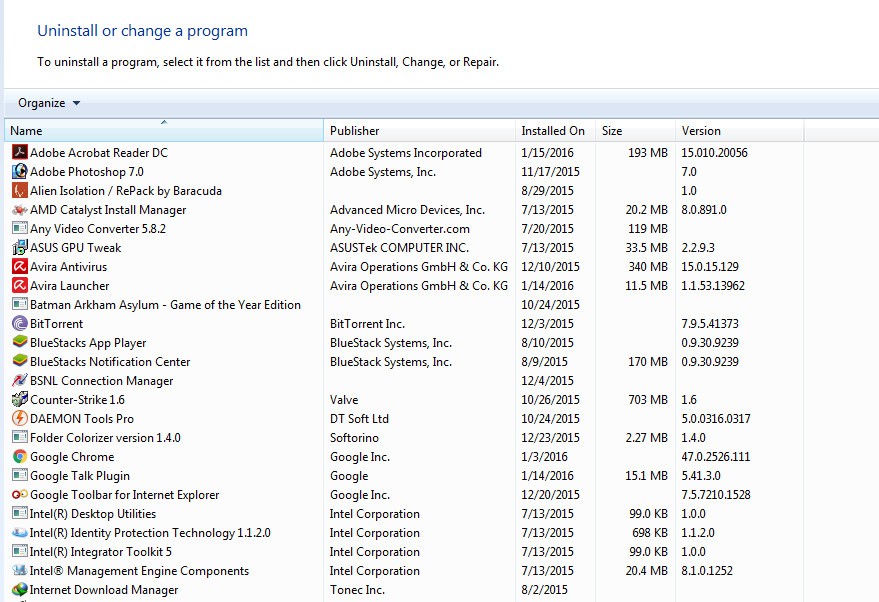
When these programs are removed, the keylogger will also be removed from your system, and you are now in a "safe" state.
In some cases, users can apply the solution of using the support of a third-party application to completely remove the keylogger on their system. Currently, there are many Anti-Rootkit tools available on the market, but which tool is the most effective is worth mentioning.
Here are 3 of the best tools you can check out:
- Malwarebytes Anti-Rootkit Beta:
Malwarebytes Anti-Rootkit Beta (MBAR) is a free tool designed to help users quickly detect and remove Rootkis - types of malware that operate in a hidden and sophisticated mode on the system.
Malwarebytes Anti-Rootkit Beta is cutting-edge technology to detect and remove the worst malicious rootkits. The archive also includes a handy utility to repair damage caused by the presence of rootkits. This requires a reboot to apply the fixes.
How to use:
- Norton Power Eraser:
Norton Power Eraser is a simple solution to detect and remove malware and viruses that cannot be detected using traditional methods.
- Kaspersky Security Scan:
Kaspersky Security Scan has the ability to scan the system at extremely fast speed, helping you check if there are any viruses, malware or spyware on the system so that you can promptly find ways to destroy these viruses and malware.
Download Kaspersky Security Scan to your computer and install it here.
Once you have ensured that no one else is logged into your computer, it is important to check for any suspicious Internet connections to your device. To do this, open the Windows command line in admin mode and type the following:
netstat -b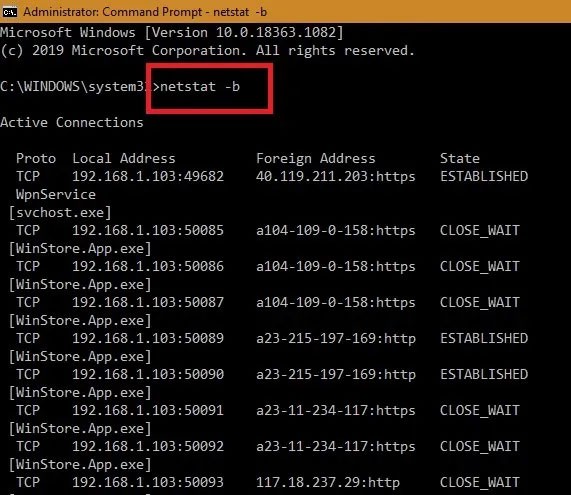
All websites and software that are connected online to your Windows computer are now visible. Apps that are connected to the Windows Store, Edge browser, or other system apps like “ svchost.exe ” are harmless. Check your IP address online for any suspicious remote locations.
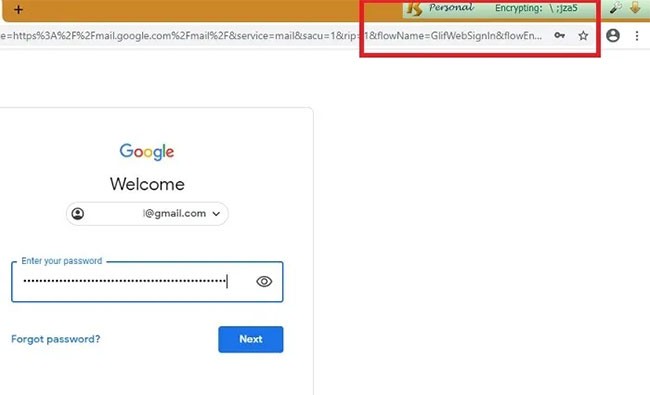
Keystroke encryption is a great way to prevent keyloggers, by encrypting all keystrokes before they are sent online. If you are the victim of a hypervisor-level keylogger attack, the malware will only be able to detect the encrypted random characters.
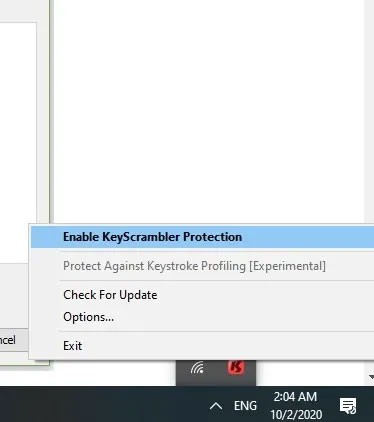
KeyScrambler is one of the popular keystroke encryption solutions. It is virus-free and safe to use with over a million paid users. The Personal version of the software is free and can secure keystroke data on over 60 browsers.
Once installed, you can activate KeyScrambler from the right system tray.
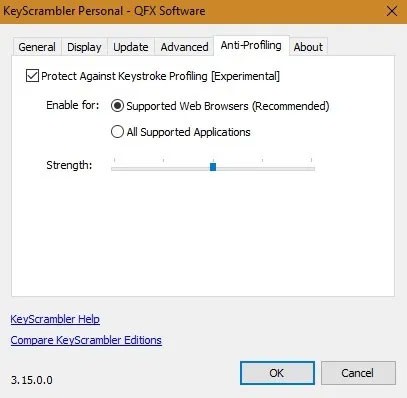
In Settings , you can protect against keystroke logging. This is done by using a typing rhythm censorship feature to protect your anonymity from websites that try to profile the way you type.
As soon as you enter keystrokes in any browser like Google Chrome or Firefox, KeyScrambler will encode all the keystrokes which you can see directly on the screen.
Finally, you should also check your web browser settings for any suspicious changes. Keyloggers often interfere with browser settings to capture keystrokes, so review all settings carefully and make sure they haven’t been tampered with or changed without your knowledge.
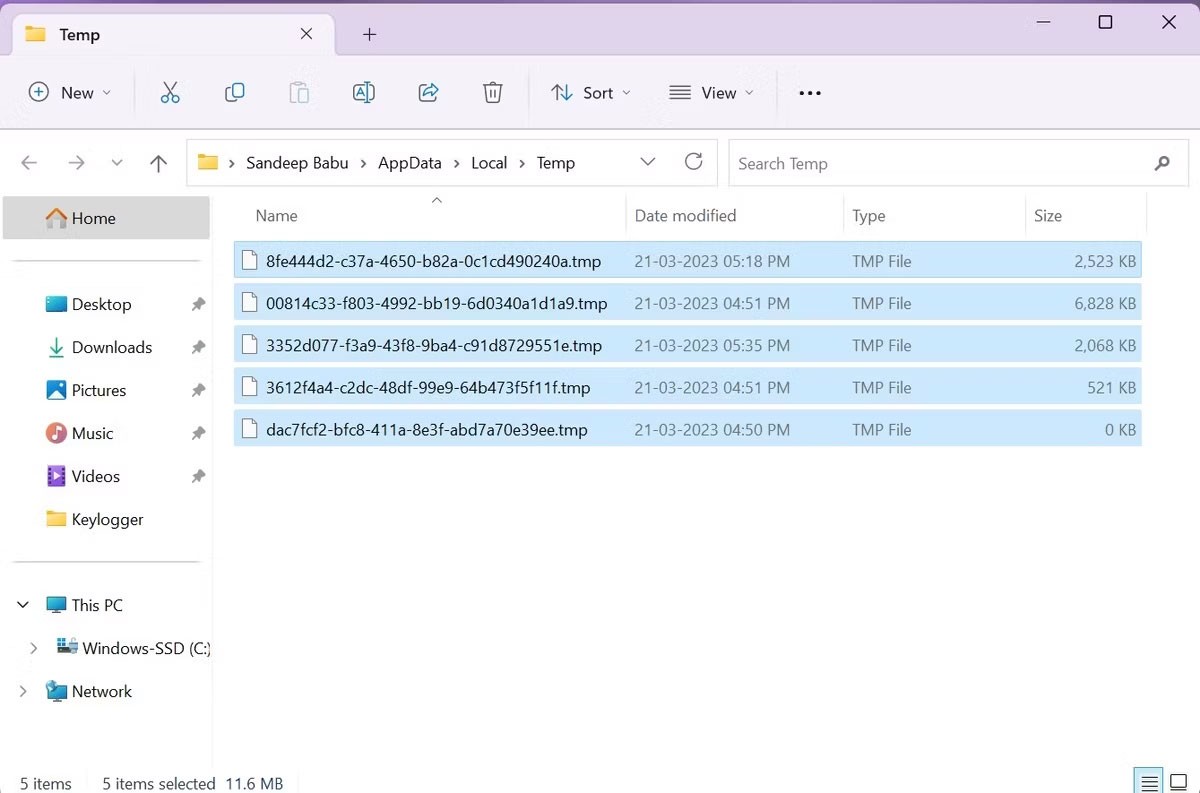
Keyloggers sometimes hide in temporary files to avoid detection, especially those downloaded from malicious websites. So you should also check your temporary files for any suspicious programs.
Since temporary files are often too cluttered to detect any suspicious programs, it's best to delete all temporary files on your PC.
Close all running programs on your PC. Press Windows + R and type "%temp%". Click the OK button. This will open the temporary files folder. Select all the files and delete them.
Keyloggers can disguise themselves as legitimate programs, so you should scan your PC with a reputable antivirus program to see if it has a keylogger.
While Microsoft Defender provides reasonable security, you should consider purchasing a paid antivirus software program to enhance your PC's security.
If you have done the above methods but still suspect that a keylogger is installed on your computer, you can use safe mode with networking to work. To enter safe mode with networking, press F8 when turning on the computer and use the arrow keys to find this mode, then press Enter to select. When accessing safe mode with networking, you are only allowed to run files on your operating system and stop all other activities, so the keylogger installed on the computer will no longer be able to track you.
This is one of the extremely useful features that you should not miss.
There are some keyloggers that are so dangerous that they can only be detected by professional methods. So, to keep your data safe from keyloggers, you should use notepad while entering usernames and passwords in login forms. Save the usernames and passwords in notepad and then copy them to your browser. Because some keyloggers do not have permission to record the keystrokes of notepad.
If you have important, sensitive data stored on your computer, it is important to protect it from these keyloggers. It can take a lot of time to find and detect a keylogger because it can come from the Internet because many software are downloaded from unofficial websites. It is also worth your attention to find a safe source to download software , and when installing software, make sure you monitor the entire process to avoid installing unwanted tools.
The most effective way to remove a keylogger is to use an anti-malware tool. Run a full scan of your system and follow the program's instructions to remove any malicious files it finds. You can also use a dedicated anti-spyware program to more accurately detect keyloggers.
Protecting your PC from keyloggers is essential to ensure the security and privacy of your data. Now that you know how to check for keyloggers, the next step is to harden your PC to prevent keylogger attacks. Additionally, to protect your sensitive data, you should be wary of another information-stealing malware called FormBook .
Good luck!
See more articles below:
Struggling with Microsoft Edge YouTube error like black screen and lag? Discover step-by-step fixes for smooth playback. Clear cache, toggle hardware acceleration, and more – ultimate guide to resolve black screen and lag issues fast.
Master how to completely uninstall Microsoft Edge from Windows 11 in 2026. Step-by-step, no-trace removal for gamers seeking max performance. Say goodbye to bloatware!
Discover how to reset Microsoft Edge to default settings in 2026 effortlessly. Fix crashes, slowdowns, and pop-ups with proven step-by-step methods for a fresh, blazing-fast browser.
Tired of Microsoft Edge "Certificate Not Trusted" warnings blocking your browsing? Discover proven troubleshooting Microsoft Edge "Certificate Not Trusted" warnings steps to resolve SSL errors securely and regain smooth access. Works on latest Edge versions.
Discover how to safely remove your Microsoft Edge profile and personal data without risks. Our expert guide ensures a clean slate while protecting your important info – perfect for privacy pros!
Discover simple, step-by-step instructions on how to change Microsoft Edge home page and startup settings. Customize your browser for a faster, personalized experience today!
Tired of Microsoft Edge update errors crashing your Windows 11 browsing? This ultimate guide delivers proven, step-by-step fixes for common issues like 0x80070005, stuck updates, and more. Update Edge effortlessly today!
Struggling with "This Site is Not Secure" error in Edge? Discover step-by-step fixes to restore secure browsing instantly. Clear cache, update certs, and more—no tech skills needed!
Tired of the frustrating Microsoft Edge "404 Not Found" error? Discover quick, proven fixes to resolve 404 errors in Edge browser. Step-by-step guide with latest tips for smooth browsing.
Tired of Microsoft Edge "Out of Memory" error crashing your streaming sessions? Get step-by-step fixes to resolve it fast, boost performance, and stream smoothly without interruptions. Updated with the latest tips.
Struggling with Troubleshooting Microsoft Edge "Cortana and Copilot" AI? Get proven fixes for crashes, unresponsiveness, and errors in the latest Edge versions. Restore your AI assistant effortlessly!
Struggling with the Edge Browser "Clock Behind" error on Windows 11? Discover proven, step-by-step fixes to sync your clock, clear caches, and restore smooth browsing. Quick solutions that work!
Tired of Microsoft Edge video stuttering and frame drops ruining your streaming? Discover proven troubleshooting steps to restore smooth playback in this comprehensive guide. Fix it fast!
Struggling with the Microsoft Edge BitLocker recovery loop error? Discover simple, step-by-step fixes to escape the endless loop and regain access to your PC without data loss. Updated with the latest solutions.
Struggling with the Microsoft Edge "Core Isolation" Settings Error? Discover proven step-by-step solutions to resolve it fast, restore smooth browsing, and boost your PC security. Works on latest Windows versions.