How to Check Purchase History on Apple App Store
Through your purchase history on the App Store, you will know when you downloaded that app or game, and how much you paid for the paid app.
A surprising discovery of the security flaw is the smartphone motion sensor embedded in their hardware.
Even if you are very careful about security when using phones and other devices, there are risks that you do not realize. Security researchers regularly find new threats that allow malicious agents to access a user's personal data.
An unexpected discovery of security holes from motion sensors in smartphones embedded in their hardware. These sensors are designed to detect when the phone is moving and in use. But they can be misused.

Security researchers have recently demonstrated a scary flaw in Android phones. This attack, called Spearphone, could collect data from speakers. Therefore, it has the ability to eavesdrop on conversations when the phone is placed nearby. It uses the accelerometer motion sensor, to measure acceleration, tilt or rotation of the device. Location apps like Google Maps use the accelerometer to determine your location.
Spearphone works by turning this component into a microphone. The accelerometer is placed on the same plane as the phone speaker, allowing it to capture echoes generated by the speech. When someone uses their phone in speaker activation mode or interacts with a smartphone assistant like Google Assistant , the accelerometer can record the echo of the voice. The attacker can then forward the logs to their server.
Through arXiv, researchers discovered the flaw that demonstrated how it works by creating a malicious Android application. They then tested the app on devices including LG G3, Samsung Galaxy S6 and Samsung Galaxy Note 4. It can record speech using the accelerometer, send audio recordings to. servers that researchers control. Then automatically analyze the record by machine learning software.
Using the data collected in this way, the researchers were able to determine the speaker's gender in 90% of cases and accurately identify the speaker 80% of the time.
According to a report by Trend Micro, a group of different security researchers have discovered two Android apps that do this. These are Currency Converter and BatterySaverMobi , which appear as useful tools to convert currencies and track your phone's battery. But in reality, they contain a banking malware called Anubis , which steals credit card data and online banking credentials.
These applications took advantage of motion sensors to evade detection. When security researchers search for malware, they often run tests on a virtual operating system stored on a computer. This means that the motion sensors do not sense any movement during the test, but when users install an application on their mobile phone, they usually hold their phone with them. Obviously, this creates a lot of movement that the sensor receives.
Malicious applications check for vibration using motion sensors. If motion is not detected, they understand that the application is being tested and do not deploy any malicious code. Therefore, security researchers will not find anything suspicious. But when a user installs an application and one of the above and starts moving around, it will turn on malware and may start stealing your data.

Another security issue you've probably heard of is browser fingerprinting. That's when data from your computer and browser is used to identify and track yourself. For example, it may work by viewing the different browser extensions you have installed and the fonts you use on your computer. This data can be used to build a unique picture of users and follow them on the Internet.
Both iOS and Android devices can face security risks from using motion sensors. Using a technique called SensorID, it can create fingerprints using the gyroscope and magnetometer sensor data from your phone. These sensors are calibrated in a unique way for each user, meaning they can rely on them to identify you. If apps or websites have access to a user's motion sensor, they can track when they use the Internet.
This technique works even when you take security precautions, such as using a VPN or using another browser. More frightening, it still exists after users perform a factory reset on the phone. The reason is that the calibration fingerprint of your motion sensor never changes. According to the researchers, this is a fast attack, taking less than 1 second to create fingerprints.
These attacks are very hard to counter. However, there are some steps you can take to protect yourself from the security risks of abusing motion sensors on your phone.
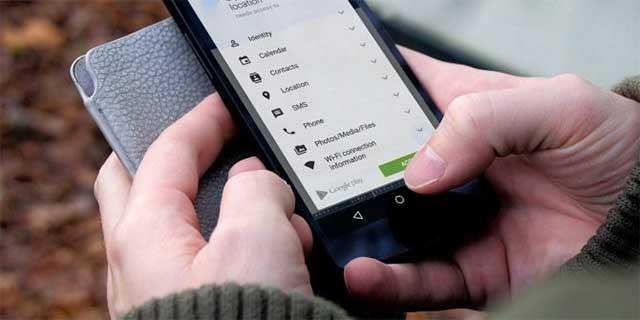
First, be careful when granting permission to an application. When you install a new app from Google Play , it asks the user for permission to use various functions on the phone. For example the camera application will require access to the mobile camera.
Many users agree to allow permissions without even realizing and this is at a very high risk of security risks. Next time you install a new app or game on your phone, check what permissions it requires. If it requires permission to use your phone's motion sensor, ask yourself what it needs that permission for. If there is no good reason for an application to need access to it, do not install it.
Secondly, if you are really worried about the motion sensor being abused to eavesdrop on your conversations, users can perform many direct actions such as adding anti-vibration material around the phone speakers to prevents the motion sensor from capturing the echo. Also, avoid leaving the phone on a flat, hard surface like a table when using the speaker. This will prevent the accelerometer from obtaining sound information.
To protect against fingerprint security risks, it is best to ensure the phone operating system is always up to date, as this issue has been resolved in operating systems such as iOS 12.2 . Google has also been aware of the problem and is working hard to update the Android system to protect users.
Always be vigilant and protect your information by using your smartphone intelligently. Hope this article will be helpful to help you use your phone safer and more secure!
Through your purchase history on the App Store, you will know when you downloaded that app or game, and how much you paid for the paid app.
iPhone mutes iPhone from unknown callers and on iOS 26, iPhone automatically receives incoming calls from an unknown number and asks for the reason for the call. If you want to receive unknown calls on iPhone, follow the instructions below.
Apple makes it easy to find out if a WiFi network is safe before you connect. You don't need any software or other tools to help, just use the built-in settings on your iPhone.
iPhone has a speaker volume limit setting to control the sound. However, in some situations you need to increase the volume on your iPhone to be able to hear the content.
ADB is a powerful set of tools that give you more control over your Android device. Although ADB is intended for Android developers, you don't need any programming knowledge to uninstall Android apps with it.
You might think you know how to get the most out of your phone time, but chances are you don't know how big a difference this common setting makes.
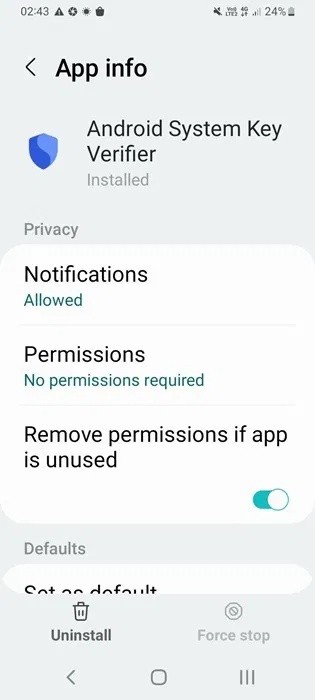
The Android System Key Verifier app comes pre-installed as a system app on Android devices running version 8.0 or later.
Despite Apple's tight ecosystem, some people have turned their Android phones into reliable remote controls for their Apple TV.
There are many reasons why your Android phone cannot connect to mobile data, such as incorrect configuration errors causing the problem. Here is a guide to fix mobile data connection errors on Android.
For years, Android gamers have dreamed of running PS3 titles on their phones – now it's a reality. aPS3e, the first PS3 emulator for Android, is now available on the Google Play Store.
The iPhone iMessage group chat feature helps us text and chat more easily with many people, instead of sending individual messages.
For ebook lovers, having a library of books at your fingertips is a great thing. And if you store your ebooks on your phone, you can enjoy them anytime, anywhere. Check out the best ebook reading apps for iPhone below.
You can use Picture in Picture (PiP) to watch YouTube videos off-screen on iOS 14, but YouTube has locked this feature on the app so you cannot use PiP directly, you have to add a few more small steps that we will guide in detail below.
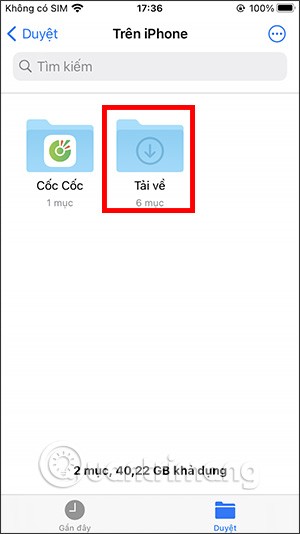
On iPhone/iPad, there is a Files application to manage all files on the device, including files that users download. The article below will guide readers on how to find downloaded files on iPhone/iPad.
If you really want to protect your phone, it's time you started locking your phone to prevent theft as well as protect it from hacks and scams.