Microsoft is about to build the worlds most powerful quantum computer

Microsoft remains a major force in global quantum computing research.
The article tested 3 different passwords with an open source password cracking tool to find out which method really works when it comes to password security.
Table of Contents

When you create an account with an online service, the provider typically encrypts your login information on their servers. This is done using an algorithm to create a “hash,” a seemingly unique random string of letters and numbers for your password. Of course, it’s not actually random, but a very specific string of characters that only your password could generate, but to the untrained eye, it looks like a jumbled mess.
It's much faster and easier to turn a word into a hash than to "decode" the hash back into a word. So when you set up a password, the service you're logging into will run your password through the hash and store the result on their servers.
If this password file is leaked, hackers will try to find out its contents by cracking the passwords. Since encrypting passwords is faster than decrypting them, hackers will set up a system that takes potential passwords as input, encrypts them using the same method as the server, and then compares the results to the password database.
If the hash of a potential password matches any entry in the database, the hacker knows that every attempt matches the potential password tried.
Let’s try cracking some of the passwords this article has generated to see how easy it is. To do this, we’ll use Hashcat , a free and open source password cracking tool that anyone can use.
For these tests, the example will crack the following passwords:
Now, let's encrypt the passwords using MD5. Here's how the passwords would look if they were in a saved password file:
Now, it's time to crack them.
To start, let's perform a Dictionary Attack, one of the most common password attack methods. This is a simple attack where a hacker takes a list of potential passwords, asks Hashcat to convert them to MD5, and sees if any of them match the three entries above. For this test, let's use the file "rockyou.txt" as our dictionary, which was one of the largest password leaks in history.
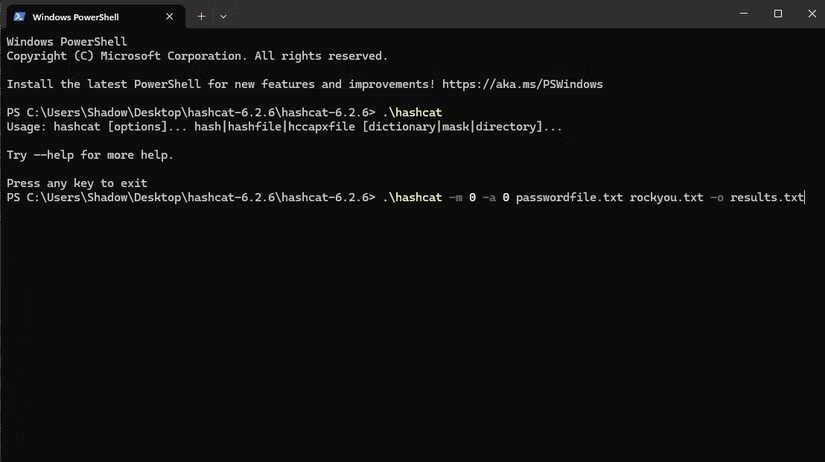
To start cracking, the author of the article went to the Hashcat folder, right-clicked on an empty space and clicked Open in Terminal . Now that the Terminal was open and set to the Hashcat folder, invoked the Hashcat application with the following command:
.\hashcat -m 0 -a 0 passwordfile.txt rockyou.txt -o results.txtHere is what the command does:
Despite the large size of rockyou, Hashcat processed all of them in 6 seconds. In the resulting file, Hashcat says it cracked the password 123456, but the passwords Susan and Bitwarden were not cracked. This is because 123456 was used by someone else in the rockyou.txt file, but no one else used the passwords Susan or Bitwarden, meaning they were secure enough to survive this attack.
Dictionary Attacks are effective when someone uses the same password as one found in a large password list. They are quick and easy to perform, but they cannot crack passwords that are not in the dictionary. Therefore, if you really want to test your password, you need to use Brute Force attacks.
While Dictionary Attacks are just taking a pre-set list and switching them one by one, Brute Force attacks do the same but with every conceivable combination. They are harder to execute and take longer, but they will eventually crack any password. As we will soon see, that can sometimes take a very long time.
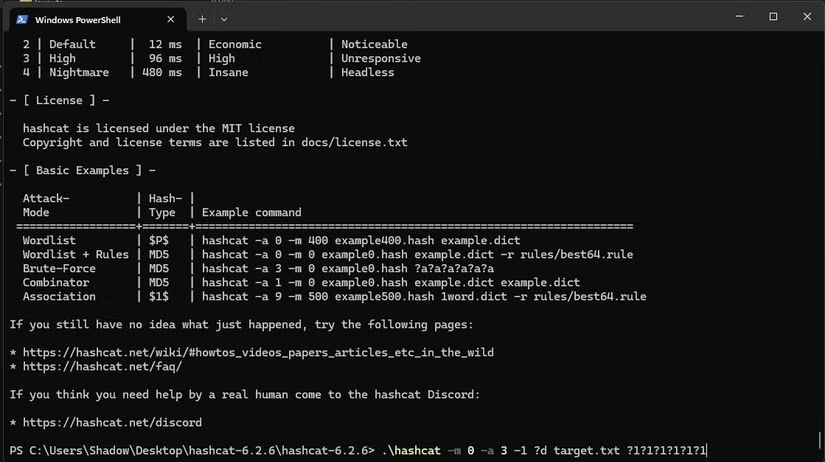
Here is the command used to perform a "real" Brute Force attack:
.\hashcat -m 0 -a 3 target.txt --increment ?a?a?a?a?a?a?a?a?a?a -o output.txtHere is what the command does:
Even with this terrible mask, the password 123456 is cracked in 15 seconds. Despite being the most common password, it is one of the weakest.
The password "Susan48!" is much better - the computer says it will take 4 days to crack. However, there is a problem. Remember when the article said that Susan's password had some serious flaws? The biggest flaw is that the password is constructed in a predictable way.
When we create passwords, we often put specific elements in specific places. Imagine the password creator Susan tried using “susan” at first but was asked to add a capital letter and a number. To make it easier to remember, they capitalized the first letter and added the numbers at the end. Then, perhaps a login service asked for a symbol, so the password creator tacked it on at the end.
So, we can use a mask to tell Hashcat to only try specific characters in specific places to exploit how easy it is for people to guess passwords. In this mask, "?u" will only use uppercase letters in that place, "?l" will only use lowercase letters, and "?a" represents any character:
.\hashcat -m 0 -a 3 -1 ?a target.txt ?u?l?l?l?l?a?a?a -o output.txtWith this mask, Hashcat cracked the password in 3 minutes and 10 seconds, much faster than 4 days.
The Bitwarden password is 10 characters long and doesn't use any predictable patterns, so it took a Brute Force attack without any masks to crack it. Unfortunately, when asking Hashcat to do so, it gave an error saying that the number of possible combinations exceeded the integer limit. The IT security expert said that the Bitwarden password would take 3 years to crack, so that was good enough.
The main factors that prevent the article from cracking a Bitwarden password are its length (10 characters) and unpredictability. Therefore, when creating a password, try to make it as long as possible and distribute symbols, numbers, and uppercase letters evenly throughout the password. This prevents hackers from using masks to predict the location of each element and makes it much harder for them to crack.
You're probably familiar with the old password adages like "use a character array" and "make it as long as possible." Hopefully, you know why people recommend these helpful tips—they're the key difference between an easy-to-crack password and a secure one.
Tired of Microsoft Teams crashing due to msvcp140.dll missing errors? Discover proven, step-by-step fixes to restore smooth video calls and chats. Works on Windows 10/11 with latest updates.
Tired of Microsoft Teams Meeting ID not working? Get instant fixes for join errors on desktop, mobile, or web. Step-by-step troubleshooting with latest updates to rejoin meetings seamlessly. No tech skills needed!
Struggling with Microsoft Teams "Welcome Error" startup loop? Discover step-by-step fixes to resolve the issue quickly. Clear cache, reset app, and more for seamless Teams experience. Updated with latest solutions.
Stuck with Microsoft Teams "Disabled Error" Account Blocked? Discover proven, step-by-step solutions to fix the issue fast, regain access, and prevent future blocks. No tech skills needed!
Master how to use Microsoft Teams Copilot for AI-powered meetings. Step-by-step guide with latest tips to generate recaps, answer questions, and boost productivity effortlessly. Transform your Teams experience today!
Master Microsoft Teams Breakout Rooms with this beginner-friendly tutorial. Step-by-step guide to creating, managing, and optimizing breakout rooms for dynamic 2026 meetings and workshops. Boost engagement now!
Stuck with Microsoft Teams Recording Save Error? Get instant, step-by-step fixes for saving recordings effortlessly. Proven solutions for all common issues – no tech skills needed!
Discover how to create a Wiki page in Microsoft Teams effortlessly. This ultimate guide covers step-by-step instructions, tips, and best practices to boost your team's knowledge sharing and productivity. Perfect for beginners!
Stuck on Microsoft Teams "Error S" screen? Discover proven, step-by-step solutions to fix Microsoft Teams Error S fast. Clear cache, restart, update & more for seamless teamwork. Works on latest versions!
Struggling with Microsoft Teams proxy error on Windows 10? Discover step-by-step fixes to resolve proxy authentication issues, connection failures, and more. Get Teams running smoothly in minutes with our expert guide.
Tired of Microsoft Teams Town Hall Event Error ruining your events? Get step-by-step fixes for scheduling, access, and registration issues. Restore seamless virtual town halls today with our ultimate guide.
Discover the simplest way to download Microsoft Teams for Mac, MacBook Air, and MacBook Pro. Step-by-step instructions, system requirements, and troubleshooting tips for seamless installation in the latest version. Get started now!
Stuck with Microsoft Teams Web Login Error? Get instant fixes for common issues like "Something went wrong" or login loops. Step-by-step guide to resolve Teams web login problems and stay productive. Updated with latest browser tweaks.
Struggling with Microsoft Teams Error 657rx Update Failed? Discover step-by-step fixes, from quick restarts to advanced troubleshooting, to get your Teams app updated and running smoothly in minutes. No tech skills required!
Tired of Microsoft Teams "VDI Error" Lag freezing your video calls? This ultimate guide delivers step-by-step fixes for VDI environments like Citrix and VMware. Optimize performance now for lag-free collaboration!