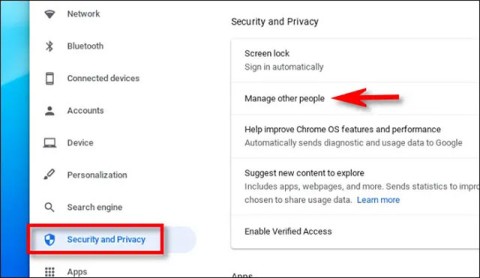
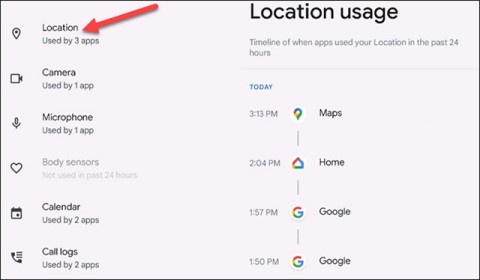
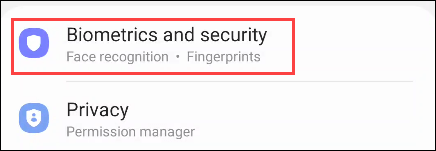
How to Check Which Apps Are Accessing Your Photo Library on iPhone
Do you remember how many times you installed an app, quickly tapped Allow on the prompt asking for photo access, and moved on without a second thought?