Security and privacy are becoming increasingly important concerns for smartphone users in general. Apple is one of the pioneers in introducing major, more optimized security features on its devices. Apple's move has received a very positive response from the user community, and this has naturally made another big name, Google, unable to ignore it.
On Android 12 , which is coming out this year, Google will introduce a very important new privacy feature that can be considered a breakthrough in the ability to ensure privacy for users. This feature is called “Privacy Dashboard”, and we will learn about it right away.
What is Privacy Dashboard?
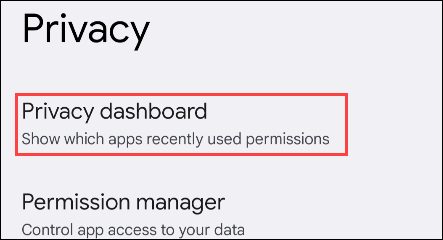
Privacy Dashboard is a privacy feature introduced by Google for Android 12. Through Privacy Dashboard, users can clearly see which applications are accessing their data, as well as choose what information the application is allowed to access.
In addition, the Privacy Dashboard also provides specific information about access activities related to personal data types on the device in real time. Users can monitor access activities to private data on the device for 24 hours, and decide whether they need to modify permissions for specific applications. Not only third-party applications, even Google applications will be fully listed in the list.
How does the Privacy Dashboard work?
As the name suggests, Privacy Dashboard is essentially a dashboard that allows users to manage everything related to privacy on their Android device. The Privacy Dashboard page will show which apps are using which permissions, and how often they are using them.
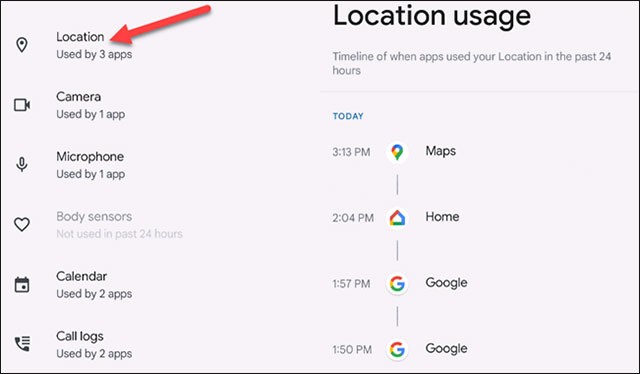
When you access the Privacy Dashboard in the Settings menu, you’ll see a dashboard open up with two different sections. The first is a pie chart at the top of the screen. This chart lets you quickly see which privacy permissions have been used the most by apps on your device over the past 24 hours.
For example, in the example, you can see that the “Location” permission is used the most, followed by “Camera” and “Microphone”. This chart correlates to the list of permissions in the section below, so if you expand to “See Other Permissions”, those permissions will also appear in the chart.
Here are all the permissions that can be tracked in the Privacy Dashboard:
- Location
- Camera
- Microphone
- Sensor
- Calendar
- Call log
- Contacts
- Files and Media
- Nearby Devices
- Phone
- Physical activity
- SMS Messages
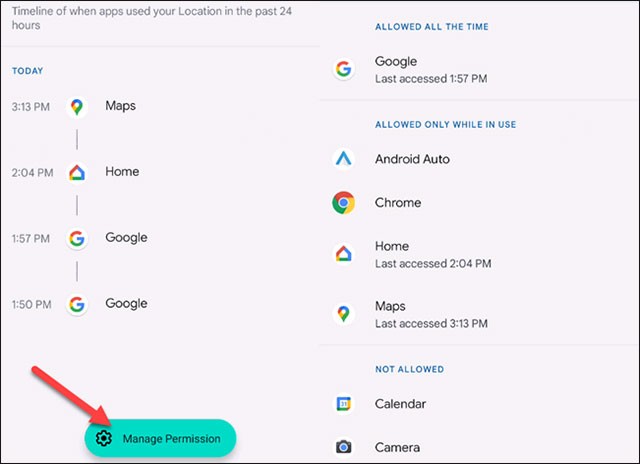
Below the chart is a list of permissions. Each permission is labeled with how many apps have used it in the last 24 hours. Click on a specific permission to see detailed usage history for that 24-hour period.
The “Manage Permissions” button will take you to a menu where you can adjust how specific apps use permissions on your device.
Where to find Privacy Dashboard on Android?
As mentioned above, Privacy Dashboard was introduced in Android 12. You will need a phone or tablet running Android 12 or later to be able to use this feature.
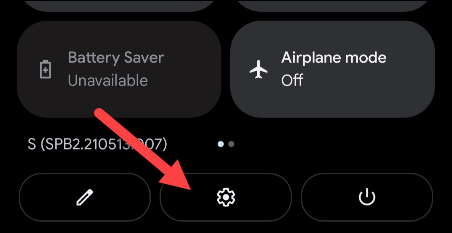
First, swipe down from the top edge of the screen to bring up the quick settings menu, then tap the gear icon.
In the Settings menu, scroll down to the “ Privacy ” section
Find “ Privacy Dashboard ” and click on it.