If you're worried about someone unwanted using your Chromebook without your permission, there's a workaround: Turn off guest access on Chrome OS.
When you turn this feature off, only registered accounts can use your Chromebook. It's super simple to do.
First, open the Chrome OS Launcher by clicking the small circular button in the bottom left corner of the screen. Then, expand the Launcher window interface by clicking the up arrow button near the top.
Once the Launcher window is fully expanded, find the “ Settings ” item (the gear icon) and select it. (You may have to scroll to the second page of the Launcher window to find this icon.)
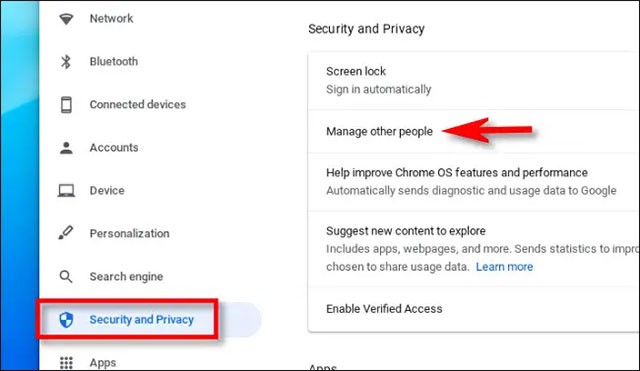
In the Settings window that opens, click on “ Security and Privacy ” on the right menu of the screen, then select “ Manage Other People ”.
Now, click on the switch next to “ Enable Guest Browsing ” to turn this feature off. When turned off, the switch will turn gray and point to the left.

Close Settings and the next time you sign out, you’ll notice that the “Browse as Guest” option is gone from the sign-in screen. Only registered accounts can use the device. Your Chromebook is now much more secure.