What is 3uTools? How to install and use 3uTools in detail

3uTools supports users to manage utility applications more than the traditional way. Easy-to-use interface, will bring interesting experiences to you.
If one day your computer suddenly restarts continuously, or maybe your computer hangs without any way to run smoothly even though you have checked and found that your hardware has no problems, then Has your computer ever been infected with viruses and what are they and what viruses on your computer will harm you? WebTech360 will introduce you to the top 6 most dangerous computer viruses of all time for you to know and find ways to avoid.
Computer viruses (often referred to by users as viruses) are pieces of program code designed to do at least two things:
Interfere with the current computer's valid operation, to perform self-replication and other work as intended by the programmer. After the execution of the virus code is finished, control is returned to the executing process without the machine "hanging" , unless the virus intentionally crashes the computer.
Self-replicating, ie self-replicating, legally infects specific files (files) or regions (boot, FAT sectors) on storage devices such as hard disks, floppy disks, devices flash memory (commonly USB),... even the main EPROM of the machine.
In the past, viruses were often written by some knowledgeable people who wanted to prove their abilities, so often viruses took actions such as: for a program to not work properly, delete data, damage the hard drive, ... or make nasty jokes.
New viruses written in recent times no longer perform pranks or damage the infected victim's computer, but are mostly directed at stealing sensitive personal information (codes). credit card numbers) open the back door for hackers to gain control or other actions to benefit the virus spreader.
Over 90% of viruses have been found to target systems using the Windows family of operating systems simply because it is the most used operating system in the world. Because of the popularity of Windows, hackers often focus on them more than other operating systems. There is also a view that Windows has less security than other operating systems (such as Linux) so there are more viruses, but if other operating systems are as popular as Windows or the market share of horizontal operating systems Equally, the amount of virus appearing is probably about the same.

What is a computer virus?
Computer viruses are program codes written by organizations or individuals for malicious purposes such as feeding data, information, blackmail, etc., and are often infected via USB, Email, or over the network. Internet. Computer viruses are always hiding everywhere and can infect your computer at any time.
The first computer virus called the Morris worm was created by a Cornell University student. This virus was released online in 1988 and has caused a series of computer damage, estimated damage up to $ 100 million and this Morris worm can also be considered the most dangerous computer virus of all time.
This malware slows down thousands of computer systems by duplicating files in temporary directories. Once infected with the Morris worm your computer will be disabled too within 90 minutes. And it takes a lot of time for computer experts to completely remove this malware.
Melissa - the most dangerous computer virus of all time was created by a man named David L. Smith in 1999. Melissa computer virus was created from the idea of based on macros in Word and this malware mainly weak are retrieved via email. This virus will entice you to open a document on email and when you open this file you accidentally activate the virus to replicate and it will automatically send to people around in the recipient email list.
The Melissa virus is spreading rapidly and damaging government private networks. This virus is so scary that Intel, Microsoft and other software companies have to shut down their email systems to avoid the damage that software brings. Total estimated damage that this Melissa virus brings up to 300-600 million USD, this is indeed the most dangerous computer virus of all time.
Code Red is an extremely malicious and rapidly spreading computer virus in 2001. This worm mainly infects computers running IIS (Web Internet Information Server) network server software. The Code Red worm has the ability to find weaknesses on IIS to infect the virus, then they will continue to infect other failed servers. After about 20 days, this malware will attack and not allow DoS to access certain IP addresses, including the White House servers. In less than a week, the Code Red virus has infected more than 400,000 servers and the number of computers attacked by this virus shows no sign of decreasing.
Sasser and Netsky are two malicious programs created by Sven Jaschan in 2004. These two worms will have different ways of transmitting and causing harm. The Sasser worm will randomly scan IP addresses and trick you into downloading virus software to your computer. When malware is downloaded, it changes the operating system and makes it difficult to shutdown. For Netsky it will be transmitted by email. When entering the computer, this virus software will attack DoS and crash websites.
Another most dangerous computer virus of all time is the Storm Worm. This virus attacked and infected millions of computers in 2006. The malware is spread by email by creating headlines that make readers curious and click on a link to watch. At this point, the malicious Storm Worm virus is downloaded to your computer, hackers can control your computer activities and spread spam emails everywhere.
Nimda is also in the top of the most dangerous computer viruses of all time and raged in 2001. The speed of this virus is terrifyingly fast, with only 22 minutes it has been remembered by the whole world. The Nimda virus infects mainly servers, and sometimes they also infiltrate personal computers. The purpose is to cripple the internet and get personal information on the server. The attack of this malware has caused great damage to software systems and brought down a series of servers around the world.
Hopefully with the 6 most dangerous computer viruses of all time you will know how to avoid hearing these names, all 6 of these viruses are really dangerous, so you should really take precautions to avoid making mistakes. Serious mistake, leading to computer problems. If you have any problems related to viruses, please contact WebTech360 .
3uTools supports users to manage utility applications more than the traditional way. Easy-to-use interface, will bring interesting experiences to you.
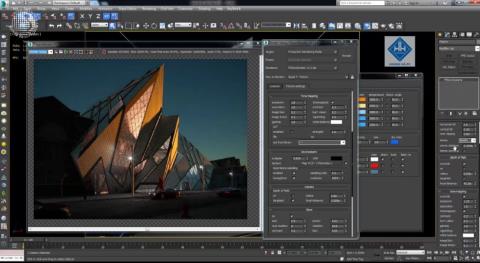
Rendering is the process of creating an image from a model into a movie scene or image using computer software.
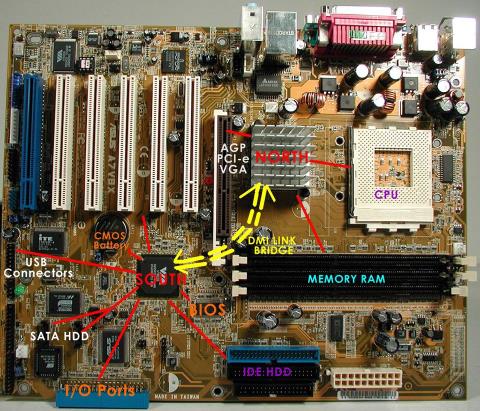
The CPU is the data processing center, or simply understood, it is the brain that controls most of the rest of the components in a computer.
The GPU is the processor that handles graphics-related tasks for the CPU's central processor. Features on GPUs go far beyond basic graphics drivers like Intel's GPU
Flyer is a form of advertising, a marketing product that has existed for a long time, also known as leaflets, product marketing brochures.
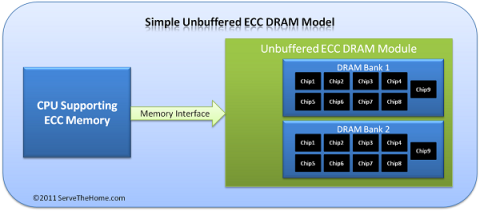
ECC RAM is a type of RAM that has the ability to control the flow of data accessed in it to help automatically correct errors. ECC RAM has very high stability which helps you to reduce risk.
Ray Tracing is a technique that helps a computer create an image by tracing the path of light through pixels on the same image plane.
Chipset is a collection of chips, chipset refers to the chip on the mainboard or on the expansion card. On PC, commonly known as northbridge and southbridge.
Hyper threading is a hyper-threading technology and is known as Intel HT technology by globally famous technology manufacturer Intel.
The VRM circuit is the voltage regulator in the motherboard. With the presence of VRM, the CPU and GPU will be provided with clean power to operate stably.
On the quality screen, they integrate a technology called V-Sync, FreeSync. Let WebTech360 explain to you about V-Sync, what is FreeSync?
Anti-aliasing is the main adjustment mode to help objects and people become softer and not angular, the game experience will also be better.
Animation is an age-old method in which people make motions of images based on still images.
Footage is unedited raw footage and footage. You can understand that footage is all the components that make up a video, and footage is very diverse.
Storyboard is a storyboard, consisting of a series of illustrations and accompanied by notes about what is going on, carrying the content of the story.
Tired of Microsoft Teams OneDrive Error blocking file sync? Follow our step-by-step guide to solve Microsoft Teams "OneDrive Error" File Sync issues quickly. Proven fixes for smooth collaboration in Teams channels. Get your files syncing error-free today!
Tired of Microsoft Teams workflows and Power Automate errors halting your productivity? Get step-by-step solutions to common issues like authentication failures, timeouts, and flow errors. Fix them in minutes and automate effortlessly!
Facing Microsoft Teams "Download Error" on MacBook? Discover proven troubleshooting steps to resolve download failures quickly, from cache clears to reinstalls, and get back to smooth teamwork.
Tired of the frustrating Microsoft Teams "Where is Teams" Folder Error? Discover proven, step-by-step troubleshooting fixes to resolve it quickly and restore smooth teamwork. Latest methods included!
Frustrated by Microsoft Teams JavaScript Error on desktop app? Discover proven steps to fix it fast: clear cache, update, reset, and reinstall. Get back to seamless collaboration in minutes!
Struggling with Microsoft Teams "Guest Login" Error? Discover step-by-step fixes, from quick cache clears to admin settings, to resolve guest access issues fast and collaborate seamlessly. Updated with the latest tips!
Tired of the Microsoft Teams "For PC" download error blocking your work? Follow our proven, step-by-step guide to resolve it quickly and get Teams running smoothly on your PC today.
Struggling with Microsoft Teams "Windows 7" login error? Discover step-by-step fixes for this frustrating issue on Windows 10/11. Clear cache, edit registry, and more – get back to seamless collaboration today!
Tired of Microsoft Teams Error Code 0x80070005 blocking your meetings? Follow this 2026 guide with step-by-step fixes for access denied issues. Get Teams running smoothly in minutes!
Master the installation of the Microsoft Teams Add-in for Outlook 2026 effortlessly. Boost your productivity with seamless scheduling and meetings. Follow our proven, up-to-date steps for instant success!
Struggling with Microsoft Teams "License Error" 2026? Discover proven, step-by-step solutions to resolve it fast. Clear cache, check licenses, and get back to seamless collaboration—no IT help needed!
Whether youre in your 50s, 60s, or even 70s, its not too late to prioritize your health and put yourself first. Here are the best exercises for people 50 and older.
Struggling with Microsoft Teams Error Caa50024 on Windows 10/11? Follow our step-by-step fixes to resolve crashes and launch issues quickly. Latest proven solutions for seamless teamwork.
Stuck with Microsoft Teams login error AADSTS50011? Discover proven, step-by-step fixes to resolve the reply URL mismatch issue and log in seamlessly. No tech skills needed!
Tired of the frustrating Microsoft Teams "Win 7" Compatibility Error blocking your meetings? Get instant fixes with our step-by-step guide, including workarounds for older Windows versions. Resolve it now and stay connected!