What is WiFi? How does WiFi work?
WiFi is a form of local area networking and wireless Internet access used by people around the world to connect their devices to the Internet without cables.
While Wi-Fi security is more advanced in 2025, it's not perfect. The following threats continue to emerge, so think twice before browsing on an unknown connection.
1. Old Wi-Fi protocols still exist
Many people still use public Wi-Fi networks normally to send emails and watch videos, seemingly oblivious to the potential risks.
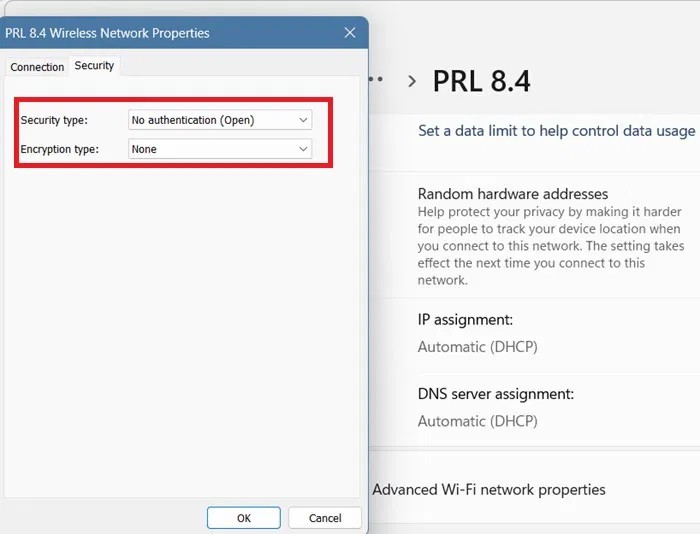
In addition to open Wi-Fi networks, you can still find older protocols like WEP and WPA. If you're in a hurry, you might connect to these networks without verifying their integrity. These older networks have weak encryption and are vulnerable to hacking and session hijacking tools.
To help you stay safe, here are a few different methods for checking your Wi-Fi network's encryption on Windows, Android, iOS, and Mac—especially useful if you're traveling internationally or living as a digital nomad .
2. Lack of Forward Secrecy – A Challenge with WPA2
The biggest challenge with WPA2-AES or WPA2-TKIP is the lack of forward secrecy. Public Wi-Fi networks continue to use simple passwords that are shared with everyone. Anyone with access to this key can decrypt all past or future sessions on the network.
Penetration tools like Wireshark provide a glimpse into captured SSL/TLS traffic. If someone has access to the server key, they can decrypt all the data. This can potentially expose login credentials, emails, etc., so using a VPN is important on public Wi-Fi networks as it encrypts all your data transmissions.
WPA3 is the gold standard for Wi-Fi security, providing strong protection against the above attacks. It uses Simultaneous Authentication of Equals (SAE), which encrypts each user session separately. You may have encountered this at airports, where a unique session key is generated after you share your passport number.
While WPA3 is highly secure, unfortunately it will take a few more years before it is widely used in public places.
3. The real problem of fake hotspots
As many frequent travelers have begun to notice, fake hotspots are becoming a big problem in hotels and other public places. Essentially, anyone can create a fake SSID to mimic the original SSID provided by your location.
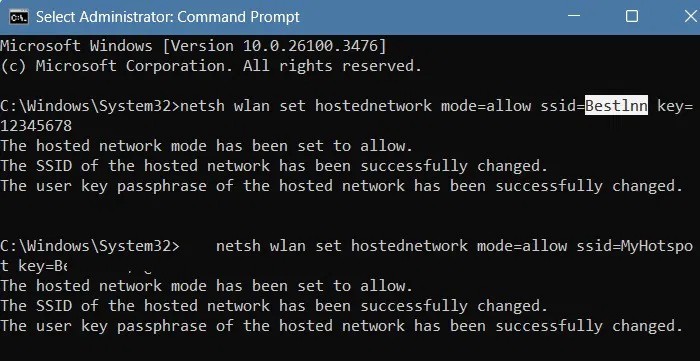
All the crooks have to do is enter a set of commands that look similar to the original Wi-Fi hotspot. For example, instead of a hotel name like “Best Inn,” the “I” might be replaced with a lowercase “L.” Hackers even copy captured portals and logos to give it an authentic look.
Again, the best way to spot a fake hotspot is to check the Wi-Fi encryption protocol it uses. Of course, they won’t use WPA3 to protect your session. If there are multiple hotspots with the same name, you’ll need to use a VPN or one of the alternatives.
4. Beware of hijacked browser sessions
Most websites today use HTTPS , but that doesn't mean all information is safe from hackers. HTTPS protects the content of your communication, but not the metadata.
If you’re using a public Wi-Fi network on secure WPA3, you’d think all the security holes would have been patched. But hijacking can attack your device on a public network – even if you’re on a very secure connection. Session hijacking involves hackers taking over your browsing data through account takeover (ATO) attacks or malware, which can originate on the dark web .
The human factor is one of the biggest reasons behind these attacks. Your identity is at the heart of device security. On Android, you can use Identity Check to prevent your device from being taken over. Similarly, iOS, Windows, and Mac devices also use biometric authentication to prevent your accounts from being taken over.
Safety precautions when using public Wi-Fi
While the risks of public Wi-Fi have decreased significantly compared to a few years ago, they are still very common in 2025. However, you can still use public Wi-Fi, as long as you remember to keep the following safety precautions in mind:
WiFi is a form of local area networking and wireless Internet access used by people around the world to connect their devices to the Internet without cables.
To make your mobile hotspot stand out and be easier to find, you can give it a unique and distinctive name.
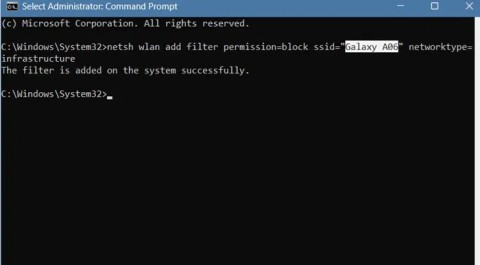
You can completely hide a Wi-Fi network or prevent it from showing up again. You can also block all other Wi-Fi networks, allowing your computer to only show and connect to the Wi-Fi networks you want easily.
To ensure better security, devices running Android 10 and above will use random WiFi MAC addresses by default.
When you want to connect to wifi in a public place, you will find some wifi networks with the word Guest, this is the guest network, also known as the Guest Network. In this article, we will learn more about the guest network as well as how to set up this network for the Router.
Most Wi-Fi routers today want to apply Beamforming technology to improve Wi-Fi transceiver capabilities, avoid interference, and increase connection speed for terminals. So what is Beamforming, how does it work? This article will introduce you to the Beamforming technology.
Since 2015, the MU-MIMO concept appeared with the promise of a technology that speeds up to 4x faster than traditional routers. The following article will help you better understand MU-MIMO technology.
When you use the network, especially the Wifi network, the slow and losing network phenomenon is unavoidable, there are many causes of this unpleasant phenomenon, possibly due to the network operator, the connection line. unstable connection, user download overload, and
Frustrated with the endless Microsoft Teams Update Error loop? Discover step-by-step fixes to resolve stuck updates, clear cache, reinstall, and more. Get back to seamless collaboration fast!
Encountering Microsoft Teams "Download Error" on your phone? Get instant fixes for Android & iOS. Clear cache, update apps, and more—back to chatting in minutes without frustration!
Struggling with Microsoft Teams VOIP connection error? Discover step-by-step fixes to solve Microsoft Teams VOIP connection error instantly. Network tweaks, cache clears, and more for seamless video calls.
Tired of the frustrating Microsoft Teams 'Unexpected Error' on startup? Discover step-by-step fixes, from clearing cache to advanced resets, to get Teams running smoothly again. Quick, reliable solutions for Windows and Mac users.
Tired of Microsoft Teams "Download Error" Unexpected blocking your workflow? Follow our expert, step-by-step guide with quick fixes and advanced tips to resolve it instantly. No reinstall needed!
Oil heaters make noise, leak oil, and do not heat up. These are all problems that arise when using a heater. So what are the causes of these problems? Read our article below!
Master how to assign participants to breakout rooms in Microsoft Teams with this step-by-step guide. Boost meeting engagement, automate assignments, and troubleshoot like a pro for seamless virtual collaboration.
Struggling with Microsoft Teams "Price Error" after the latest pricing update? Discover step-by-step fixes to resolve it quickly, restore seamless collaboration, and avoid subscription headaches. Updated with the newest solutions.
Struggling with Microsoft Teams Background Error Transparency? Discover proven step-by-step fixes for blurry, glitchy virtual backgrounds. Restore perfect transparency in Teams meetings effortlessly. Updated with the latest solutions.
Struggling with Microsoft Teams "Đăng nhập" login error? Discover step-by-step fixes for smooth sign-in. Clear cache, update app, and more – no tech skills needed! Works on Windows, Mac, and web.
Tired of Microsoft Teams Web Error 503 Service Unavailable blocking your meetings? Discover quick, step-by-step fixes to resolve the 503 error fast – no tech skills needed! Clear cache, check status, and get back to collaborating seamlessly.
Stuck with Microsoft Teams Update Error 0x80070002? Discover proven troubleshooting steps to resolve this frustrating issue quickly and get your Teams app updated seamlessly for uninterrupted collaboration.
Tired of Microsoft Teams Error AADSTS50020 blocking your sign-in? Discover step-by-step fixes for user account conflicts, backed by the latest Azure AD solutions. Get back to work fast!
Tired of Microsoft Teams microphone error with no sound? Discover quick, step-by-step fixes for Teams mic not working on Windows, Mac, and more. Restore crystal-clear audio in minutes!
Tired of the Microsoft Teams "Task Management" Error disrupting your workflow? Discover proven fixes like clearing cache, updating Teams, and troubleshooting permissions to get back to seamless collaboration in minutes. Updated with the latest solutions.