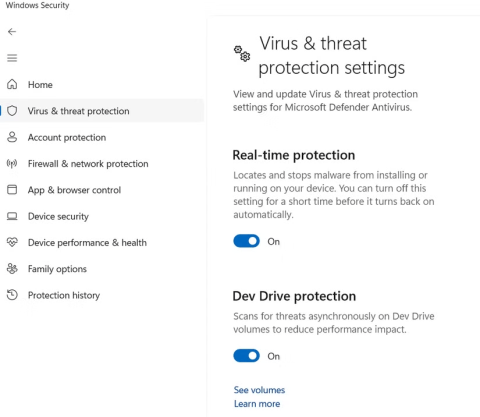
Analyzing an Attack (Part 1)

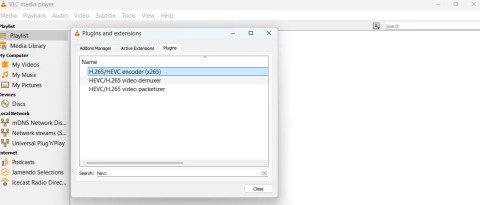
This series will be based on a network vulnerability. What will be introduced in the article is already a real attack, starting from reconnaissance to enumeration, exploiting network services and ending with exploitation strategies sending notifications. All these steps will be observed at the data packet level, and then explained in detail.