Cybercriminals are spreading malware using... Google Search

A new attack campaign that spreads malware through Google search results has been discovered by security experts from Palo Alto Networks.
When it comes to digital scams, the last thing you think of is physical mail. However, some crafty scammers have figured out how to trick people into installing malicious apps that steal their banking details, and it all starts with a hand-delivered letter in the post. But how do they do it, and how can you stay safe?
Scammers impersonate official agencies to spread malware that steals money from banks

Switzerland is being hit by malware that is being “spread” via physical mail, The Register reports. The attack begins with a fake letter claiming to be from the Federal Meteorological and Climate Office, asking the recipient to download an app. The app is a malicious clone of Alertswiss, a legitimate app that warns people about severe weather patterns.
The letter provides the victim with a QR code, through which they can download the fake app. After scanning the code, it does not open Google Play to download the app; instead, it takes the user to a third-party website. If the target proceeds to download the app, it begins intercepting the two-factor authentication code and attempts to access the victim’s bank account through their banking app. From there, the scammer can transfer money to their account.
Luckily, you can easily protect yourself from this scam. First, remember that there are many security risks when scanning QR codes. Only scan a code if you are sure it comes from an official, trusted source.
Additionally, the safest way to download Android apps is to use the Google Play Store. Legitimate companies will usually release their apps through official channels, so if a company asks you to download them through a third-party site, be cautious. And if you do download and install a malicious app, factory reset your Android phone immediately.
A new attack campaign that spreads malware through Google search results has been discovered by security experts from Palo Alto Networks.
Nowadays, malicious links appear more and more and are shared through social networks at a dizzying speed. Just clicking on a malicious link can bring potential dangers to you.
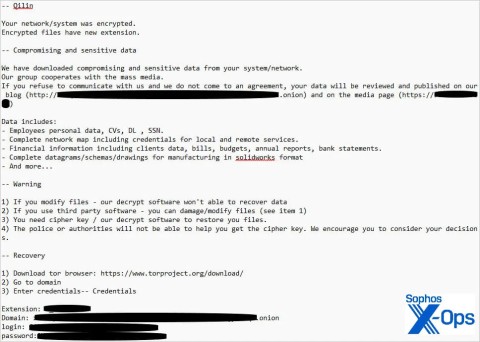
A new strain of ransomware called Qilin has been discovered using a relatively sophisticated, highly customizable tactic to steal account login information stored in the Google Chrome browser.
Microsoft has just officially warned users about the existence of a vulnerability that could allow hackers to easily spread malware through the Outlook email application.
A cybersecurity firm has discovered a huge number of Android apps containing malicious code (adware), a discovery that also raises big questions about how Google monitors its online store.
Nowadays, free wifi networks are installed everywhere, from coffee shops, amusement parks, shopping malls, etc. This is very convenient for us users to be able to connect to the network everywhere to surf Facebook and work. However, is using free wifi safe?
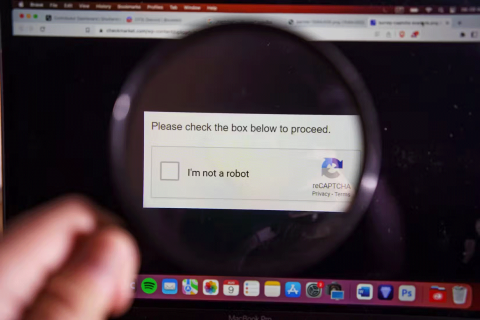
Unfortunately, bad actors know this and have created fake CAPTCHAs that will infect your PC with malware.
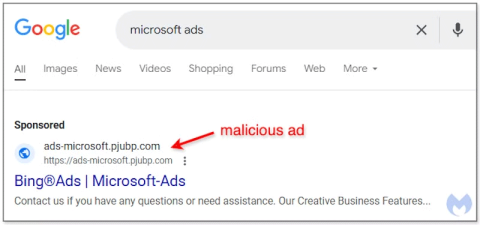
There is a dangerous trend being deployed by the global hacker community, which is abusing the Google Ads platform to spread malicious code.
Stuxnet is a malicious computer worm that was first discovered in June 2010 after it paralyzed Iran's nuclear facilities. And to this day, Stuxnet is still a terrifying obsession for the global Internet.
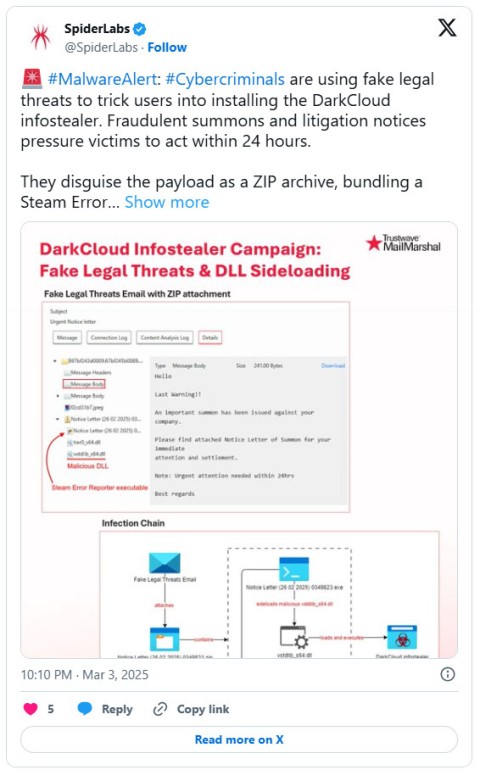
Often distributed in a malware-as-a-service model, infostealer malware is often used to steal data, remaining hidden for as long as possible.
Why is new malware being developed to hide from users, and what does that say about the current cybercrime world?
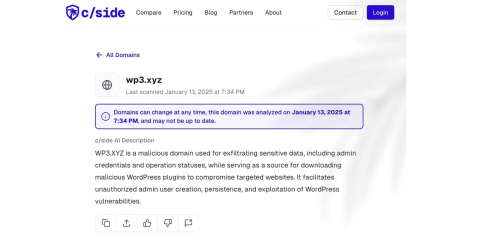
As one of the most popular website building tools in the world, WordPress is once again a target for malware.
Even though Windows 10 will stop being supported after October 14, 2025, many Steam users are still using the operating system.
Keyloggers are extremely dangerous programs that hackers install on any user's system with the aim of stealing passwords, credit card information, etc. Keyloggers store all the keystrokes that users perform on the computer and provide hackers with important user information.
Tired of the frustrating Microsoft Teams "Check Version" error blocking your meetings? Follow our proven, step-by-step fixes to resolve it fast and restore smooth teamwork. Works on latest versions!
Struggling with the wrong Microsoft Teams account on Windows 11? Discover simple, step-by-step instructions to remove and change your Microsoft Teams account effortlessly. Perfect for managing work and personal profiles!
Struggling with Microsoft Teams "Guide" Tutorial Error? Discover simple, step-by-step fixes to resolve it quickly. Clear cache, update, and more for seamless teamwork. Updated for latest versions!
Struggling with Microsoft Teams for Mac sync errors? Follow this ultimate troubleshooting guide with step-by-step fixes to resolve sync issues quickly and get back to seamless collaboration on macOS. Updated with the latest solutions.
Tired of the frustrating Microsoft Teams "Website Error" loading issue? Follow our proven, step-by-step fixes to resolve it fast and restore smooth teamwork. Works on all browsers!
Struggling with Microsoft Teams Remote Control Error? Discover step-by-step troubleshooting for Remote Control issues in Teams. Quick fixes, common causes, and expert tips to get back to seamless collaboration. Updated with the latest solutions.
Struggling with Microsoft Teams "Media Error" Microphone? Get instant fixes for crystal-clear audio. Step-by-step solutions for permissions, drivers, and more – no tech skills needed!
Tired of the frustrating Microsoft Teams "Error" on your desktop shortcut? Discover proven, step-by-step solutions to resolve it fast and restore smooth teamwork. No tech skills needed!
Stuck with Microsoft Teams "Error P" password error? Discover quick, effective troubleshooting steps to resolve login issues and get back to seamless collaboration in minutes. Updated with the latest fixes.
Frustrated with Microsoft Teams "Welcome" screen stuck on Error 2026? Discover proven, step-by-step fixes to resolve it fast and get back to seamless collaboration. Updated with the latest tips!
Struggling with Microsoft Teams "Action Required" login error? Discover step-by-step troubleshooting fixes, clear cache methods, and quick solutions to get back to seamless collaboration. Updated with the latest tips for instant relief.
Facing Microsoft Teams Webinar Registration Error? Follow our proven, step-by-step guide to fix it quickly and get back to seamless webinar registrations. Latest troubleshooting tips included!
Tired of Microsoft Teams "Joining Error: Meeting Full"? Get proven, step-by-step solutions to bypass the error and join instantly. Latest fixes for seamless meetings!
Tired of the frustrating Microsoft Teams recording error: Permission Required? Follow our expert, step-by-step guide to regain recording access instantly with the latest Teams policies and fixes. No tech skills needed!
Tired of Microsoft Teams Error Report Not Sending? Discover quick, effective troubleshooting steps to resolve it fast and get back to seamless collaboration. Expert tips included!