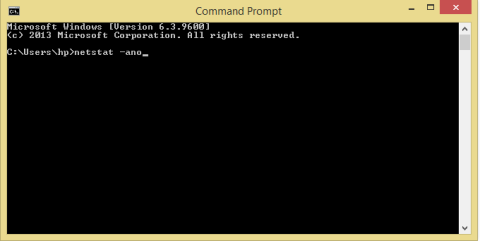
Cybercriminals are spreading malware using... Google Search

A new attack campaign that spreads malware through Google search results has been discovered by security experts from Palo Alto Networks.
They are advantages and disadvantages with the advent of technology being used in almost every angle of day-to-day lives. Technology has brought in a lot of ease in our operations at home, our offices, and businesses as well. Through the use of technology, organizations, business entities, and manufacturing industries can automate their operations such that there needs to be no physical manpower for a task to be done.
There are also disadvantages of technology in that it can fail and disrupt all the operations that relied on it. Some people have ill motives in the online space. These people are there to steal, alter or destroy someone’s, an organization’s, business entities, and manufacturing industry’s information. They do this with the motive that they will not accomplish what they had planned to do.
People that love the content on the internet will often use a Virtual Private Network to access what has been restricted in their countries. For movie and series lovers, it is through here you can find how to watch Netflix using VPN and get no restrictions on what kind of movies or series to watch. However, VPN users should always be on the lookout for online hackers who come through different ways.
Online users can get access to a computer system with no authorization. They do this by installing malware on people, organizations, business entities, and manufacturing industries' computers and computer systems. Malware is hence defined as software that brings harm to a computer, computer system, or the files saved in a computer.
7 Types of Malware Attacks and How to Prevent Them
There are numerous types of Malware attacks. This article will highlight seven types of Malware attacks and how they can be prevented.
The adware malware attack displays themselves as pop ads as a computer user is surfing the internet. If a computer user clicks on these pop ads, they immediately take you to other sites that help hackers gain access to your computer device.
Virus malware attacks come hand in hand with the formats in which one saves their computer files. It is hence important for computer users to be careful about the kind of files they download and the formats in which they save their computer files.
Another type of Malware attack is a worm that an online hacker installs in computers and computer systems. A worm is also capable of getting access to your data and being able to steal it and giving easy access to your computer and computer system to online hackers. The worm has the capability of slowing the internet bandwidth a computer user could be using for his or her internet connectivity.
A worm malware attack is also capable of giving online hackers backdoor access to a computer device. Once a worm has access to a personal computer or computer system, it is capable of spreading in all parts of a computer and deteriorating the functions of the machine. One of the major disruptions that a worm can bring to a computer or a computer system is deleting the files you have saved.
Computers users could restrict the worm malware attack from invading their computer devices and systems by limiting or giving restrictions to the number of people that visit their websites at a go.
A trojan horse is a malware attack that looks like a valid file to a computer user. It hence makes it easy for a hacker to get access to a computer device or computer system because a computer user will hardly suspect it as a file that ought not to be in his or her computer. A trojan horse malware attack can easily spy on your computer device, get access to your internet network and consequently delete and gain access to the data you have saved on your computer.
The spyware malware attack gets installed in one’s computer or computer system through pop-up ads and online activities that happen with a computer user’s knowledge. Through the spyware malware attack, hackers gain access to a computer user’s passwords and get acquainted with all the sites one visits oftentimes.
The ransomware malware attacks come in two forms the Crypto and locker ransomware. This means that hackers give themselves the power of web administrators. They can hence control who accesses their computer systems and have the capability of deleting files or data.
When a ransomware malware attack is installed in your computer device or computer system by an online hacker, a computer user can hardly get access to his files or easily use his or her computer. This hence prompts a computer user to make a payment to get back access to his or her computer files and be able to use his or her computing device. If a computer user falls into the trap and attempts to make a payment, they could easily lose all their data.
However, a computer user can avoid ransomware by changing the passwords of their website administrators oftentimes and being aware of any discrepancies that may be occurring in their files or computer systems.
The phishing malware attack gains access to a person, organization, business entity, or manufacturing industry’s computer when a computer user opens emails sent to them. Some emails sent seemingly look like they are from trusted sources but they are not. These emails could be inquiring about personal details such as bank details. A computer user could easily dish out their information and eventually have their data stolen.
It is key that computer users, organizations, business entities, and manufacturing industries that use computers be keen on their online presence. Online hackers are always on the watch and it is up to computer users to safeguard their passwords and avoid clicking on any pop-up or emails that look suspicious.
A new attack campaign that spreads malware through Google search results has been discovered by security experts from Palo Alto Networks.
Nowadays, malicious links appear more and more and are shared through social networks at a dizzying speed. Just clicking on a malicious link can bring potential dangers to you.
Some crafty scammers have figured out how to trick people into installing malicious apps that steal their banking details, and it all starts with a hand-delivered letter in the post.
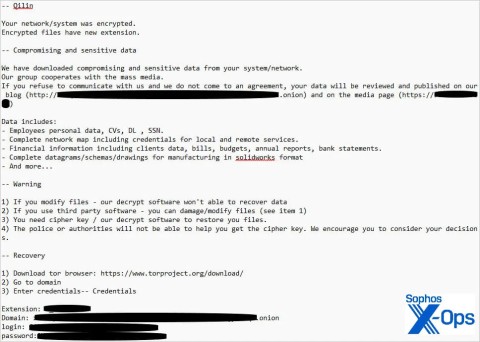
A new strain of ransomware called Qilin has been discovered using a relatively sophisticated, highly customizable tactic to steal account login information stored in the Google Chrome browser.
Microsoft has just officially warned users about the existence of a vulnerability that could allow hackers to easily spread malware through the Outlook email application.
A cybersecurity firm has discovered a huge number of Android apps containing malicious code (adware), a discovery that also raises big questions about how Google monitors its online store.
Nowadays, free wifi networks are installed everywhere, from coffee shops, amusement parks, shopping malls, etc. This is very convenient for us users to be able to connect to the network everywhere to surf Facebook and work. However, is using free wifi safe?
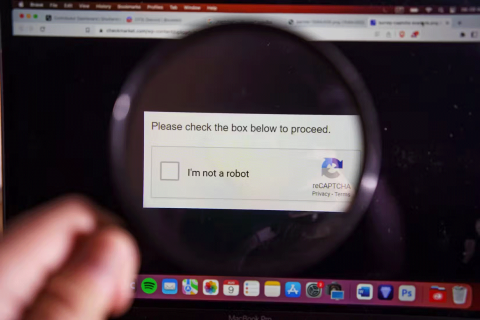
Unfortunately, bad actors know this and have created fake CAPTCHAs that will infect your PC with malware.
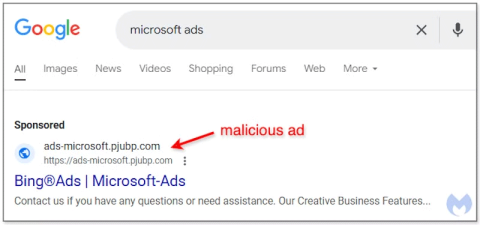
There is a dangerous trend being deployed by the global hacker community, which is abusing the Google Ads platform to spread malicious code.
Stuxnet is a malicious computer worm that was first discovered in June 2010 after it paralyzed Iran's nuclear facilities. And to this day, Stuxnet is still a terrifying obsession for the global Internet.
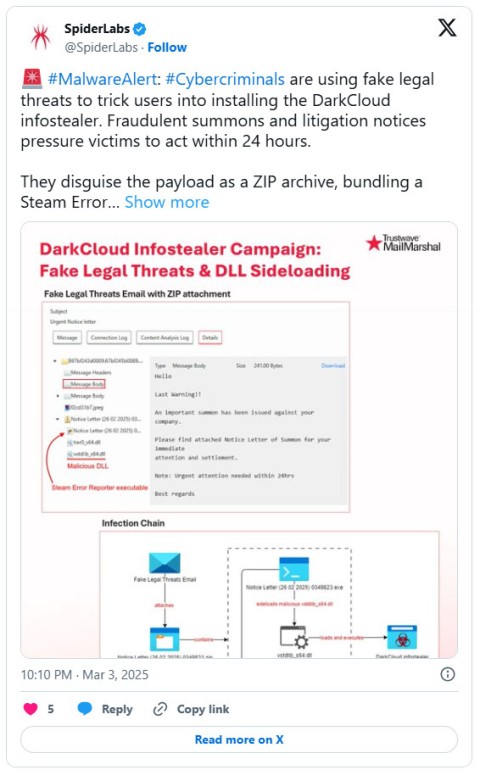
Often distributed in a malware-as-a-service model, infostealer malware is often used to steal data, remaining hidden for as long as possible.
Why is new malware being developed to hide from users, and what does that say about the current cybercrime world?
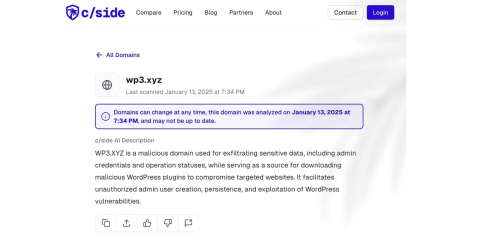
As one of the most popular website building tools in the world, WordPress is once again a target for malware.
Even though Windows 10 will stop being supported after October 14, 2025, many Steam users are still using the operating system.
Keyloggers are extremely dangerous programs that hackers install on any user's system with the aim of stealing passwords, credit card information, etc. Keyloggers store all the keystrokes that users perform on the computer and provide hackers with important user information.
Frustrated with the endless Microsoft Teams Update Error loop? Discover step-by-step fixes to resolve stuck updates, clear cache, reinstall, and more. Get back to seamless collaboration fast!
Encountering Microsoft Teams "Download Error" on your phone? Get instant fixes for Android & iOS. Clear cache, update apps, and more—back to chatting in minutes without frustration!
Struggling with Microsoft Teams VOIP connection error? Discover step-by-step fixes to solve Microsoft Teams VOIP connection error instantly. Network tweaks, cache clears, and more for seamless video calls.
Tired of the frustrating Microsoft Teams 'Unexpected Error' on startup? Discover step-by-step fixes, from clearing cache to advanced resets, to get Teams running smoothly again. Quick, reliable solutions for Windows and Mac users.
Tired of Microsoft Teams "Download Error" Unexpected blocking your workflow? Follow our expert, step-by-step guide with quick fixes and advanced tips to resolve it instantly. No reinstall needed!
Oil heaters make noise, leak oil, and do not heat up. These are all problems that arise when using a heater. So what are the causes of these problems? Read our article below!
Master how to assign participants to breakout rooms in Microsoft Teams with this step-by-step guide. Boost meeting engagement, automate assignments, and troubleshoot like a pro for seamless virtual collaboration.
Struggling with Microsoft Teams "Price Error" after the latest pricing update? Discover step-by-step fixes to resolve it quickly, restore seamless collaboration, and avoid subscription headaches. Updated with the newest solutions.
Struggling with Microsoft Teams Background Error Transparency? Discover proven step-by-step fixes for blurry, glitchy virtual backgrounds. Restore perfect transparency in Teams meetings effortlessly. Updated with the latest solutions.
Struggling with Microsoft Teams "Đăng nhập" login error? Discover step-by-step fixes for smooth sign-in. Clear cache, update app, and more – no tech skills needed! Works on Windows, Mac, and web.
Tired of Microsoft Teams Web Error 503 Service Unavailable blocking your meetings? Discover quick, step-by-step fixes to resolve the 503 error fast – no tech skills needed! Clear cache, check status, and get back to collaborating seamlessly.
Stuck with Microsoft Teams Update Error 0x80070002? Discover proven troubleshooting steps to resolve this frustrating issue quickly and get your Teams app updated seamlessly for uninterrupted collaboration.
Tired of Microsoft Teams Error AADSTS50020 blocking your sign-in? Discover step-by-step fixes for user account conflicts, backed by the latest Azure AD solutions. Get back to work fast!
Tired of Microsoft Teams microphone error with no sound? Discover quick, step-by-step fixes for Teams mic not working on Windows, Mac, and more. Restore crystal-clear audio in minutes!
Tired of the Microsoft Teams "Task Management" Error disrupting your workflow? Discover proven fixes like clearing cache, updating Teams, and troubleshooting permissions to get back to seamless collaboration in minutes. Updated with the latest solutions.